Incidents don’t fail teams, process does. Alerts fire, context is missing, and the same questions get asked while the outage clock keeps running. Without a clear incident flow, even small issues turn into drawn-out disruptions.
This post breaks down incident management as it actually happens during live outages. Detection, triage, communication, resolution, and follow-up, where teams lose time, and what usually causes repeat incidents. It’s grounded in real response patterns, not idealized playbooks.
You’ll learn how to structure incident response so signals are clear, ownership is obvious, and recovery is faster. If outages still feel chaotic, this is the place to tighten the process.
What is incident management?
Incident management refers to the process of dealing with unexpected issues or disruptions (known as ‘incidents’). If something breaks, incident management is the process of restoring normal service operations as quickly as possible.
In the world of IT service management, the official definition for ‘incident’ is an “unplanned interruption to an IT service or reduction in the quality of an IT service.” Whether that means a slowdown in response time or a total system crash, you’re looking at an incident.
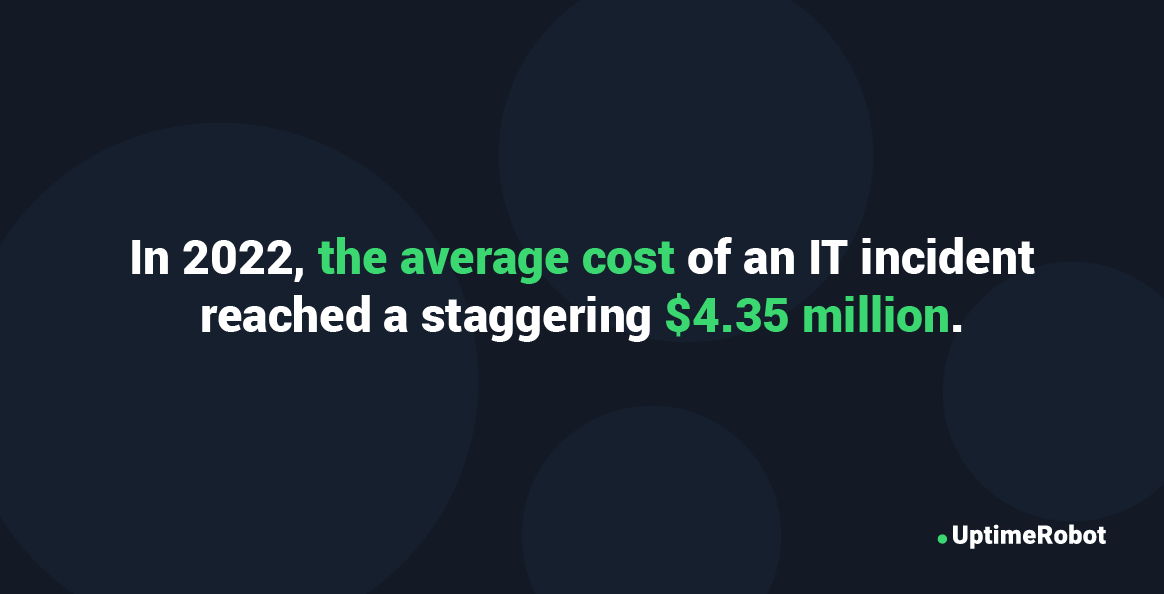
Incidents tend to have a sort of domino effect, which is why they are so expensive to deal with. A report from IBM estimates that the average cost of an IT incident in 2022 was a mouth-dropping $4.35 million.
However, incidents tend to do more than just financial damage. They also cause service disruptions, a lot of stress for your team, and a lot of headaches for the customer service people dealing with unhappy customers.
It’s fair to say you either want to avoid incidents altogether or learn to manage them well so that they don’t drive everybody crazy when they do occur.
And that’s where incident management comes in.
Why is it important?
For starters, service interruption is expensive. When websites go down, it costs companies thousands (or even millions) of dollars. Depending on the industry, this can have a cascading effect you will be feeling for months to come.
Let’s take the example of service level agreements (SLAs). CIO defines SLAs as “the level of service you expect from a vendor, laying out the metrics by which service is measured, as well as remedies or penalties should agreed-on service levels not be achieved.”
For example, availability and uptime are key parts of a website hosting SLA, so you might get a written promise of a minimum uptime of 99.99% in your contract.
If a major incident occurs, chances are you won’t be able to meet that service level agreement — which can mean fines, penalties, and loss of reputation.
Having a plan in place to deal with issues will mitigate much of the damage, but not every company is ready. A survey by FRSecure found that only 45% of the companies polled had an incident response plan in place. The rest were, more or less, just hoping for the best with no backup plan.
Incident management also improves efficiency and team productivity and helps prioritize urgent incidents, it provides insights into recurring issues and their underlying causes.
So while incident management might seem like a plan created to respond to an emergency, it should be looked at as a strategic approach to improving service quality.
By adopting best practices in incident management, you can learn and grow so the number of disruptions can decrease.
Incident Management Starts Before the Incident Exists
Incident management is often treated as something you do during an outage. In practice, most of the outcome is decided long before anything breaks.
The first step is deciding what counts as an incident. Not every alert deserves the same response. Clear severity levels prevent overreaction to minor issues and underreaction to serious ones. If everything is an incident, nothing is.
Detection quality sets the pace. Incidents start when signals cross a threshold that requires human action. Noisy alerts slow response because teams hesitate. Quiet, well-scoped alerts speed it up because people trust them. Incident management cannot compensate for poor monitoring inputs.
Ownership needs to be obvious. When an incident is declared, someone should automatically become responsible for coordination. Without a clear owner, teams lose time deciding who is in charge instead of fixing the problem. This decision should never be made mid-incident.
Communication is the next pressure point. Internally, responders need one shared place for updates and decisions. Externally, users need clear, honest status updates. Mixing those two audiences creates confusion. Good incident management separates them while keeping facts aligned.
Speed matters, but so does containment. Many incidents get worse because changes continue while the system is unstable. A defined freeze or change-control rule during incidents prevents accidental escalation and makes recovery safer.
Resolution is not the end. What matters next is learning without blame. Post-incident reviews should focus on what failed in systems and process, not who made a mistake. If reviews feel punitive, people hide information. That guarantees repeat incidents.
Over time, patterns emerge. Repeated causes, slow detection, or delayed communication point to structural issues. Incident management is effective when those patterns drive concrete changes, not just documentation.
The goal is not to eliminate incidents. It is to make them smaller, shorter, and calmer every time they happen.
Teams with mature incident management do not feel heroic during outages. They feel methodical. That is the signal the system works.
The most common challenges of incident management
Organizations often struggle with a range of challenges that can affect their ability to respond effectively to unexpected events.
These challenges can have far-reaching consequences, from delayed responses to damaged reputations.
In this section, we will take a closer look into some of the most common hurdles that organizations encounter in incident management and explore solutions to address them.
By understanding and proactively addressing these issues, organizations can improve their incident management capabilities and be better prepared to handle the unexpected.
The official definition for ‘incident’ in the world of IT service management, is an “unplanned interruption to an IT service or reduction in the quality of an IT service.” Whether that means a slowdown in response time or a total system crash, you’re looking at an incident.
Not having a preventive plan in place
One of the key challenges many organizations face is the lack of a preventive plan. Simply reacting to incidents as they come up, without an established framework or strategy to pre-empt them, can lead to delayed responses and escalated issues.
If tracking and monitoring systems are not in place, potential problems may go unnoticed until they become critical emergencies.
This gets worse if the company fails to log and track incidents because it means losing the opportunity to analyze and learn from them. This could result in recurring problems, more downtime, and increased operational costs.
Jump to the solution👉 “2. Adopt a Proactive Approach”
Not having clear channels of communication in place
When unexpected incidents happen, especially those detected by users, the lack of a streamlined way to report and address these issues can drastically affect their resolution.
If you don’t communicate with your customers, they will not know you’re currently working on resolving the issue. This can lead to frustration, loss of trust, and reputational damage.
Within the company, the lack of a structured communication system can lead to crucial details being overlooked, causing unnecessary delays, duplicated efforts, or misinformation.
Jump to the solution👉 “5. Have the Right Communication Channels in Place”
Lack of testing
Organizations that write detailed incident response logs but don’t follow up are setting themselves up for disaster. Without regular testing, they will remain unaware of potential flaws or outdated procedures in the plan.
If regular testing is absent, it can create a misleading feeling of readiness, which can easily turn into a disaster when facing actual emergencies.
For example, a plan’s designated contact person may have switched to a new role or specific response tactics might have become obsolete due to changes in technology or organizational structure.
Relying on an untested plan can lead to more incidents, miscommunication, and missed opportunities for mitigation.
Frequently testing and reviewing your incident management plan ensures it’s efficient and your company is capable of responding properly when something happens.
Jump to the solution👉 “9. Test & Review Your Plan”
Best practices to improve incident management
1. Define what “incident” means to your business
An incident is an unplanned interruption to an IT service, but the extent of what is involved can vary greatly from business to business.
If we consider an e-commerce company, it could be as simple as a website going down and preventing customers from making a purchase.
For British Airways in 2017, an outage meant over 1,000 flights grounded and 75,000 very unhappy stranded passengers.
Because the differences are so wide, it’s important to define what an ‘incident’ means within your industry. Atlassian recommends doing this by establishing KPIs (Key Performance Indicators) to “help businesses determine whether they’re meeting specific goals. For incident management, these metrics could be number of incidents, average time to resolve, or average time between incidents.”
2. Adopt a proactive approach
Adopting a proactive approach in incident management is about preparing for and preventing issues before they occur, rather than just reacting to them after the fact.
You prepare by having a team and a plan in place (more about that later) and by ensuring your technology infrastructure is up-to-date. But also by having several monitoring and alerting systems in place to identify potential issues before they escalate into full-blown incidents.
For example, with incident management tools like UptimeRobot, you can set up 24/7 monitoring to receive real-time updates and alerts if your site experiences performance issues.
You might not think of logging an incident as something preventive (after all, the incident already occurred), but keeping track of what happened as you’re working on resolving it might help prevent future problems. UptimeRobot’s Event Log feature helps you track all events related to your monitors so you can have a record of each incident, its causes, and the steps taken to resolve it. You can even leave comments for your colleagues.
By adopting a proactive approach to incident management, you’re not just putting out fires; you’re actively working to prevent them.
3. Prioritize incidents based on their impact
Think of incident prioritization as a sorting mechanism for your IT health — emergencies that have a potentially huge impact on business operations should trigger a quick response, but if your system just has a little “headache,” this should be considered a low-priority incident.
If you find yourself on the verge of panic, remember that not all incidents are created equal.
A minor glitch that disrupts for just a few minutes? Important, but not catastrophic. That server crash that causes your busy e-commerce site to grind to a halt for half a day? Panicking might be for this one.
This is where incident prioritization comes into play. According to Zapoj IT Event Management, “Effective incident management relies on the ability to focus on impact rather than the order in which issues arose.” So in a complex situation, the first incident to occur isn’t necessarily the first one that should be solved.
What’s a top-priority incident? Let’s look at some examples:
- Anything that has a significant effect on customers or users. People can’t complete online purchases? This is a high priority because it has a direct impact on revenue and customer satisfaction.
- Things that could potentially cause reputational damage. Data breaches aren’t just scary — they also break trust with customers.
- Anything that will take a long time to resolve. The more complex an incident is, the bigger the headache you’ll get trying to fix it. So if an incident doesn’t seem terrible but you’ll need six hours to get things back up and running, move this to the priority list.
Making people wait for a resolution causes customer dissatisfaction, which can then ruin your reputation, which then … you get the idea. If an incident is going to take a long time to get fixed, it should be considered a top priority.
4. Establish a strong incident response team
An incident response team is a group of people who will jump into action to restore normal service as quickly as possible after something happens — and they can be the difference between a minor hiccup in operations and a major catastrophe.
If your goal is to mitigate damage, incident management best practices suggest that you should have a comprehensive contingency plan in place for unexpected events.
A well-prepared, well-coordinated incident response team is your business’s first line of defense when an incident strikes.
According to the 2022 IBM’s Cost of a Data Breach Report, “Breaches at organizations with incident response (IR) team capabilities saw an average cost of a breach of USD 3.26 million in 2022, compared to USD 5.92 million at organizations without IR capabilities.”
Simply put, having an IR team in place can reduce the cost of an incident by about 58%.
So who makes up the ideal incident response (IR) team? There’s no one-size-fits-all answer here and the perfect IR team should match your organization’s size and nature, but you could potentially have an:
- incident manager
- technical specialists
- communication officers (somebody needs to make sure everybody else on the team is kept updated!)
- and somebody in charge of making high-level decisions as needed
Unfortunately, this is an area where many companies are failing. The IBM report reveals that “just 38% of organizations said their security teams were sufficiently staffed to meet their security management needs.”
The rest are … well, they’re just hanging on for dear life.
A properly trained IR team should be able to function without guidance when an incident occurs.
This means everybody is ready to jump into action and has a pre-assigned, specific role to solve the problem so nobody needs to make last-minute decisions about how to handle an emergency.
Here’s an example of what not to do: In 2017, Danish shipping giant Maersk was the victim of a cyberattack. The NotPetya malware caused a massive disruption that hijacked the firm’s update servers and shut down Maersk’s system, halting operations.
It took Maersk 9 days to restore its Active Directory system. One of the main reasons the damage was so extensive?
The company didn’t have an incident response team in place. After the attack happened, Maersk scrambled to assemble an IR team to work out of the UK, but by then, they had lost previous time and the work to rebuild the network ended up taking much longer. By then, the incident had cost the company between $250 million and $300 million.
Effective incident management isn’t just about responding to issues (though that would have helped Maersk significantly back in 2017), but also about being proactive with a team ready to jump into action when an incident occurs.
5. Have the right communication channels in place
Communication channels (like email, live chat, web forms, or phone) allow people to report incidents and lead to faster resolution times and better customer satisfaction.
Effective communication is the backbone of any successful incident management process, especially when incidents involve customers.
Many smaller incidents are first caught by users. For example, a customer trying to make a purchase might notice your website or app has crashed or is experiencing a significant slowdown.
They might also alert you to problems with the payment gateway, such as being unable to complete a transaction or being charged twice.
Users might also notice:
- Bugs like broken links or navigation issues
- Slow page load times
- Data Inconsistencies and content issues, including outdated information
Communication channels also add a valuable element to your incident management plan that requires no work or investment on your side and makes people feel included.
This can include:
- A status page to keep users informed, minimize support tickets, and maintain transparency.
- A way to provide regular updates for an incident that’s taking some time to be resolved.
In addition to the status page, this can be done via status updates on your website, email notifications, or even through social media channels.
6. Use of automation in incident management
Automation tools (also known as incident management systems or IMS) consist of a set of tools and processes used to identify, respond to, and resolve incidents efficiently. For example, IMS can automate routine tasks, such as incident logging and updating incident statuses so the response team can focus more on fixing the problem and less on administrative tasks.
Sometimes the automation can be very basic, such as creating a list of canned responses to be used by AI-powered chatbots to help users deal with simple issues or answer basic queries from employees.
Sometimes it can simplify things by providing multi-channel support. For example, tools like ProProfs Help Desk can track all incoming support requests by “centralizing information and support management services to handle a company’s internal as well as external support requests.”
Popular incident management software like Zendesk also offers automation features that streamline ticket routing, status updates, and internal communications, helping teams resolve incidents faster and with greater consistency.
This improves tracking and reporting, encourages collaboration among team members, and ensures everyone has access to the latest information to avoid confusion.
By incorporating automation into your incident management process, you will be simplifying processes while enhancing efficiency.
7. Have an internal system for regular updates and logs
An internal system is a combination of incident logs, response, and request headers, and monitor logs a team can use to “talk” during an incident.
These internal communication systems can dramatically improve the efficiency of your incident management process. Keeping the channels of communication open reduces confusion and stress, so every person can focus on the task at hand.
It’s not just the end-users that need to receive regular updates when you’re dealing with a disruptive incident. Everybody in the team (whether they’re working to solve the incident or are just being affected by it) needs to be kept in the loop too, with platforms like Diligent allowing you to keep senior leaders and board members informed.
Regular updates help create a proactive communication environment, reducing confusion and helping everyone stay on the same page.
This strategy also reduces the load on your support team, as end-users, being informed about the progress of their tickets, are less likely to inundate your team with additional queries.
In addition to incident logs, UptimeRobot also provides Response Headers (which can help provide clues about the incident’s origin), and Monitor Logs (also known as ‘all events’), which provide additional information about system performance and error details.
8. Maintain comprehensive and updated documentation
After an incident, you should always update your database with a detailed record of the incident and its resolution.
Going forward, this allows everybody in the company to go back to this information to understand what transpired, how it was resolved, and how similar incidents can be prevented in the future.
These databases are sometimes known as ‘runbooks’, which Squadcast defines as “a compilation of routine procedures and operations that are documented for reference while working on a critical incident.”
Simply put, a runbook is a database of knowledge organized for easy access.
Rather than trying to find a mix of documents and checklists across a mix of Google Docs, Notion, and other platforms, having a central database where all the information is collected saves valuable time when the team is working on critical incidents.
Updating documentation should also include redesigning documents or FAQ pages that are difficult to read.
Big chunks of text are challenging at any time, but during an incident, they will feel like a nightmare. So spend some time adding diagrams, bullet points, and other visual aids to complex documentation to make it easier and quicker to scan and read.
Standardizing the documentation also helps. If everything has a similar look or uses a standard template, the brain can absorb the information better and quickly.
9. Test & review your plan
Once you’ve designed a system, you need to test it repeatedly to help you identify its strengths and weaknesses and optimize strategies.
According to InvenioIT, “around 7% of organizations never test their disaster recovery plans.” And from those that do, half will only test once a year (or less frequently). This creates a false of security (“But I already have a disaster recovery plan!”) and you might end up with an even worse crisis.
Source: InvenioIT
Carrying out practice drills and updates can prevent trouble down the line, especially because they will double as practice sessions for your incident management team.
If you wait a whole year to test and update your incident response plan, you might discover some of the procedures aren’t current or key people no longer work for the company.
If part of your incident plan requires calling John when something goes wrong but John left the company three months ago and nobody found a replacement for his role, you’re in trouble. Involving relevant staff in the tests is essential to make sure everybody understands their roles during a real incident.
Plans should also be reviewed every time a real incident happens. This is the perfect opportunity to identify areas for improvement.
It’s also a good time to see if your test scenarios are realistic and reflect potential incidents your team may face.
10. Post-incident reviews and analysis
Postmortem are post post-incident reviews and analyses that are essential to help teams learn from past incidents, improve processes, and prevent similar incidents from happening again.
They also offer a chance to bring people together to discuss the details of an incident: what happened, why, the impact of it, and how we make sure this doesn’t happen again.
The process of conducting an effective post-incident review involves several steps:
Collecting and analyzing data for root-cause analysis (RCA)
Think you know everything about why an incident happened? Don’t be so sure.
Sometimes the tiniest details can make all the difference when you’re analyzing all relevant data about the incident.
So make sure you spend some time looking at incident logs, system metrics, user reports, and any other data that could provide insights into what happened and why. If you have a UptimeRobot account, you can check the Incident tab to get specific details about an incident.
Implementing recommendations for improvement
After identifying the root causes, the next step is to come up with a set of changes you can implement to prevent the same thing from happening again.
This could involve changes to systems, processes, or even staff training.
RCA shouldn’t be looked at as a blame game. You’re not in it to figure out who’s at fault for what happened but to understand why it did so you can take action. For example, leading e-commerce site Etsy conducts what they call “blameless postmortems.”
Their main focus is “to understand how an accident could have happened, to better equip ourselves from it happening in the future.” The company never places blame, reprimands, or fires people for an action that made sense to the person at the time they took it.
In short, things happen — let’s take the opportunity to learn from them.
Informing your customers of the results of your postmortem
This is key to regaining their trust after an incident. For example, in May 2023, GitHub experienced a major outage caused by a configuration change to GitHub’s internal service.
A week later, GitHub’s Chief Security Officer shared details about the incident on the company’s blog, explaining that they had since mitigated those incidents and all systems were back to operating normally and adding that “This is not acceptable nor the standard we hold ourselves to.”
An effective method to keep your users informed is by utilizing a status page. The status page allows you to communicate essential information regarding your service availability and provide updates about scheduled maintenance.
While postmortems are essential to learning from incidents so you can improve your incident management processes, they are also key to assuring your customers you are committed to doing better in the future.
Wrapping up: key takeaways & next steps
Understanding and implementing incident management best practices can significantly improve your response when unexpected events happen. This isn’t just about avoiding potential issues — it’s about turning challenges into opportunities for learning and growth.
So, where do you begin?
- Deep Dive into Best Practices: Start by doing a comprehensive review of these best practices. Then try to figure out how they can be applied in different scenarios in your own company.
- Integration with Existing Protocols: To make them more effective, make sure that these guidelines are seamlessly integrated into your existing organizational protocols. This might mean revising old guidelines or establishing new ones.
- Regular Training & Simulation: Knowledge that isn’t put to use can become obsolete. Conduct regular training sessions to ensure that all team members are on the same page. Occasionally, run simulated incident scenarios to test and improve your team’s response time and efficiency.
- Continuous Feedback Loop: After any incident, hold a debriefing session. What went well? What could have been done better? This continuous feedback loop is essential for refining your processes.
Remember, embracing these action points is not just about damage control. It’s about being proactive, resilient, and forward-thinking. Let’s roll up our sleeves and make incident management an asset in our organizational toolkit. After all, there’s a certain
FAQ’s
What is incident management?
Incident management is the process of detecting, responding to, and resolving unexpected issues that impact service availability or performance. The goal is to restore normal operations as quickly as possible. It also focuses on minimizing user impact during incidents.
Why is incident management important?
Incident management reduces downtime duration and limits customer impact. Without a clear process, alerts get missed, ownership is unclear, and recovery slows down. A structured approach makes incidents less chaotic and more predictable.
What are the key stages of incident management?
Most incident workflows include detection, alerting, response, resolution, and review. Detection identifies the issue, response assigns ownership, and resolution restores service. Post-incident reviews help prevent repeats.
How does monitoring fit into incident management?
Monitoring is the trigger that starts the incident process. It detects anomalies or outages and sends alerts to responders. Without reliable monitoring, incidents are often discovered by users instead of your team.
Who should be involved in incident response?
The primary responders are usually on-call engineers or SREs. Depending on severity, product, support, or management may also be involved. Clear roles prevent confusion during high-pressure situations.





2 Comments
I find it interesting when you said that there are various types of incidents from business to business which is why it is best to define it first. I can imagine how important that is because there would definitely be different risks for every type of organization, structure, or establishment. Also, it must be useful to have an incident command board system that your employees will use, but they have to be trained for it to log the right information to be used by professionals when helping other people.
I find it interesting when you said that updating the database should always be done with a detailed record of the situation and what was the resolution. I can imagine how important it is to use an up-to-date incident command board system if there are available new technologies these days, especially when there are different types of situations that are emerging compared to what was happening before. In my opinion, there are definitely lots of happenings these days that weren't possible before which is why using something that is more advanced would probably be more applicable.