Domain hijacking doesn’t look dramatic at first. Traffic drops, emails bounce, or users land on a page you don’t control. By the time you realize the domain was taken over, brand damage and data risk are already in motion.
This article breaks down what actually happens after a domain hijack. Lost revenue, SEO fallout, phishing exposure, and long recovery timelines show up fast, even if the takeover is brief. These are real consequences teams underestimate until they’re dealing with one.
You’ll learn how hijacking typically occurs, what the impact looks like in practice, and which warning signs appear early. If your domain is tied to trust, uptime, or revenue, understanding the fallout is the first step to preventing it.
But the right domain name can also be a money powerhouse.
You probably paid as little as $20 for your domain name, but the biggest names out there cost a lot more than that.
The most expensive domain name acquisition to date was the purchase of “Cars.com” in 2014 by Gannett, in a deal that valued the domain at a whopping $872 million.
Source: Name.com
Trailing behind are:
- CarInsurance.com ($49.7 million),
- Insurance.com ($35.6 million),
- and VacationRentals.com ($35 million).
Shocking, isn’t it?
With such huge value, it’s no surprise that domain hijacking has become a significant threat — a threat often overlooked but capable of causing immense damage if not dealt with promptly and correctly.
Understanding Domain Hijacking
Domain hijacking (also known as domain theft or domain slamming) is just what it sounds like — the takeover of a domain name from the rightful owner.
So, how common is domain hijacking?
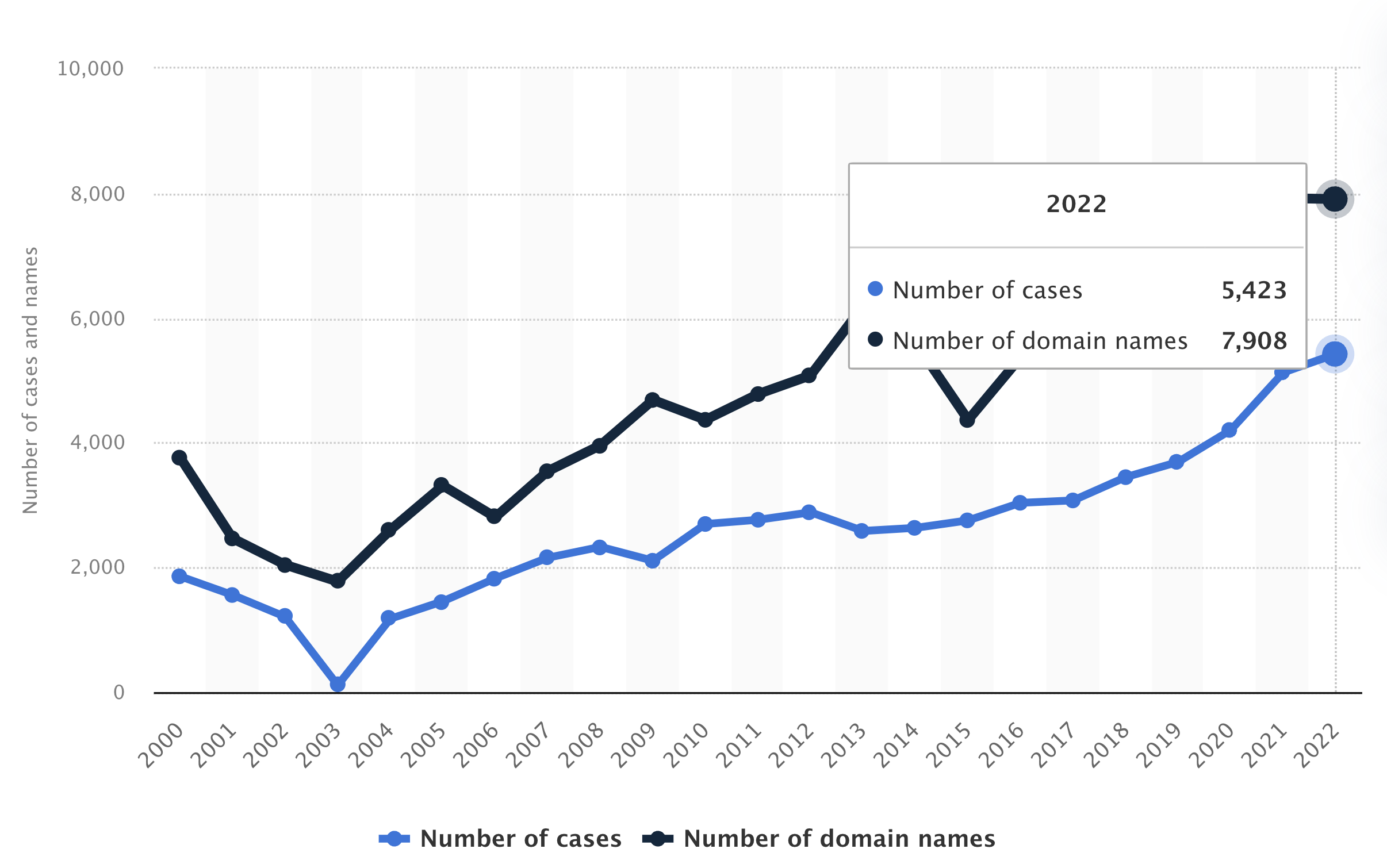
Although obtaining concrete figures is challenging, the World Intellectual Property Organization (WIPO) handled over 7000 cybersquatting cases in 2022.
The number of cases filed to the World Intellectual Property Organization has increased, especially since 2012, when there were around 2900 such disputes.
Source: Statista.com
As a general rule, hijackers tend to target domains that are either financially or strategically valuable.
➡️Financially valuable domains include short, one-word domains or those containing popular or industry-specific keywords. The Cars.com and Insurance.com examples mentioned above are great examples.
➡️Strategically valuable domains, on the other hand, are more about the value of taking over the website of successful businesses or organizations. For example, hijacking a major online retailer’s domain during peak shopping season could cause significant revenue loss for the original owner and huge financial gains for the hijacker.
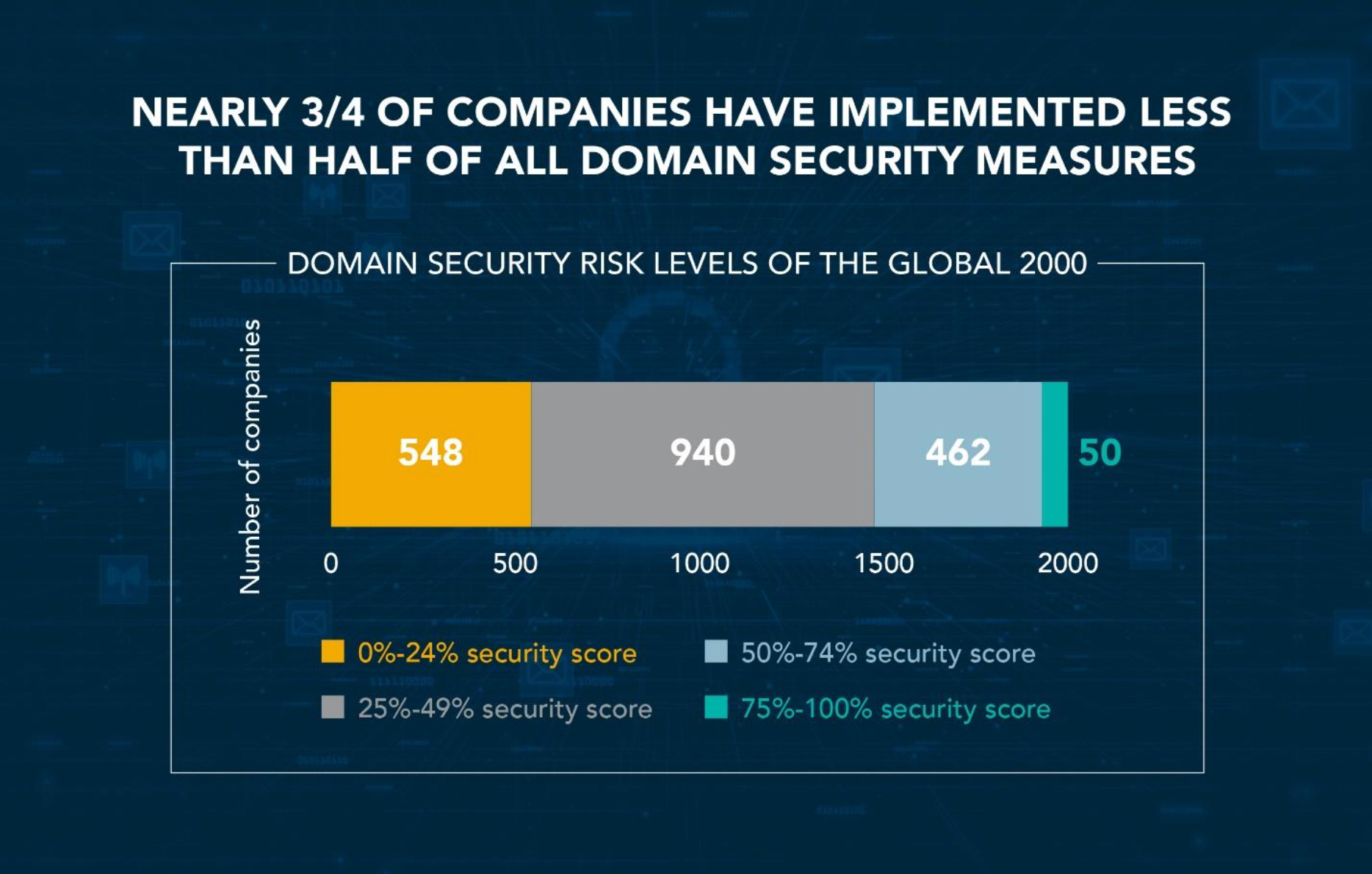
What makes a domain valuable?
✅ Has traffic
✅ Search friendly
✅ Niche relevant
✅ Brandable
✅ Popular TLD
✅ High SEO authority
✅ Generates income
The Mechanics of Domain Hijacking: A Deeper Dive
Hijackers can use many different tactics to take over a domain, including:
- phishing
- exploiting security vulnerabilities
- drop-catching expired domains
- brute-force attacks
Phishing
Phishing attacks are one of the most common ways a hijacker can gain access to a domain, perhaps because it’s so simple.
All a hijacker needs to do is send deceptive emails to the domain owner, pretending to be from the domain registrar or another trusted source.
These emails often contain links leading to fraudulent websites — and once the domain owner enters their login credentials, the hijacker can easily capture them.
Security Vulnerabilities
Security vulnerabilities in the domain registrar’s system can also serve as an avenue for domain hijacking. According to a report by Palo Alto Networks’ Unit 42, phishing and software vulnerabilities cause nearly 70% of cyber incidents.
If the domain registrar you used has weaknesses, a hijacker can break in and alter a domain’s ownership details or redirect the domain to a different server.
Domain Expiration
Another prevalent method for hijacking is related to domain expiration or ‘drop-catching’.
When a domain isn’t renewed before it expires, it becomes available for anyone to register — and this is when hijackers can snatch them within seconds of becoming available.
You can easily avoid this with Domain expiration monitoring from UptimeRobot.
Start monitoring domain expiration
Brute-force Attacks
Although less common, brute force attacks are also a possibility. This technique involves an attacker systematically attempting all possible password combinations until they find the correct one.
Proactive Steps to Safeguard Your Domain
As the saying goes, “Prevention is better than cure,” and the same rings true for securing your domain.
A strong defense involves a combination of robust security and privacy measures, as well as constant vigilance. Regularly maintaing your website is a must for online businesses.
Here are some of the most effective strategies that can serve as barriers against potential hijackers:
Employ strong, unique passwords
How secure are your passwords?
According to a 2021 National Cyber Security Centre report, “15% of the population used pets’ names, 14% use a family member’s name, and 13% pick a notable date” as their password.
Even worse, 6% of people are still using the word “password” as their password.
To prevent cybercriminals from breaking into your accounts, use a strong, unique password instead — ideally by combining upper and lowercase letters, numbers, and symbols.
You can also use a password manager to generate and store complex passwords for you.

Keep domain registration information private
When you register a domain, your information (name, email, and address) is automatically added to the WHOIS directory — and this can make you a target for domain hijackers.
To lower your risk, you can opt to pay for “domain privacy,” which replaces your personal information with the information of a forwarding service and protects your identity.
Enable Two-Factor Authentication (2FA)
Two-step verification through SMS text messages can stop 100% of all automated attacks, 96% of bulk phishing attacks, and three-quarters of targeted attacks.
Source: Google
This is because even if a hijacker manages to acquire your password, they would still need the second verification factor (like a unique code sent to your mobile device) to access your account — making it almost impossible to break into your accounts.
Lock Your Domain
Most registrars provide an option to ‘lock’ your domain.
This feature prevents any changes to the domain’s ownership or name server information without your explicit approval.
Simply put, it means nobody else but you can transfer or make modifications to the accounts connected to your domain.
Monitor domain expiration
When a domain expires, it goes into something known as “domain drop list,” where somebody else can find it and buy it.
According to The Daily Swig, “Cybercriminals can easily use dropped domains for any attack vector that exploits an organization’s identity, such as account takeovers or phishing campaigns that leverage false business invoices.”
As an illustration, let’s consider a popular gaming company that inadvertently fails to renew their domain ‘gameworld.com’.
Opportunistic attackers could seize the domain and create a deceptive website mirroring the gaming company’s legitimate site.
However, unbeknownst to users, every download link on this fake website conceals malicious files, leading to potential security risks for unsuspecting gamers.
TIP: You can track your domain expiration with UptimeRobot — and receive alerts 30, 14, 7, and 1 day before the domain expires. This gives you enough time to prevent disasters and protect all your domains from falling into the wrong hands.
The Aftermath: Why Hijacked Domains are Hard to Recover
Recovering a domain that was hijacked can be a complex and frustrating process.
Unlike physical property, digital property ownership isn’t always clear-cut and many registrars lack robust mechanisms to handle domain disputes.
There’s also the issue of international rules and regulations — it’s basically impossible to take back a domain from somebody on the other side of the world.
As a report published by Huffington Post accurately points out, “When hackers steal a web address, few owners ever get it back.”
A good example of this is what happened to the owner of the website MLA.com.
The domain was originally purchased in 1997 for a modest $600, but by 2014, it was valued at $47,000. That is, until somebody hijacked the domain.
Despite the original owner’s efforts (which included filing a lawsuit against the Russian hijacker), the domain was never recovered.
As of 2023, it is available for sale for an impressive $125,000.
Infamous Examples of Domain Hijacking
Anybody can be a target for domain hijacking, but high-profile organizations are at a higher risk simply because their domains are worth a lot more money.
Here are some crazy examples of domain hijacking you won’t believe are real.
sex.com
One of the best-known cases of domain hijacking dates back to the early days of the Internet.
It was 1995 when a hijacker stole the domain Sex.com from its rightful owner and used it to operate a pornography site.
It took several years before a U.S. District Court would order the hijacker to return control of the domain and pay the original owner a $65 million judgment.
Just in case you were wondering, the hijacker didn’t pay and instead chose to run. He was finally arrested in 2005.
p2p.com
In 2011, cybercriminal Daniel Goncalves became the first person ever to go to prison (for five years) for domain name theft.
Goncalves had stolen the domain name p2p.com (which stands for “peer to peer”) and sold it via eBay for over $100,000 to NBA basketball player Mark Madsen.
Funnily enough, Goncalves had stolen the domain the old-fashioned way: by hacking into an AOL email account and copying the login and password details for the Godaddy account where the domain was registered.
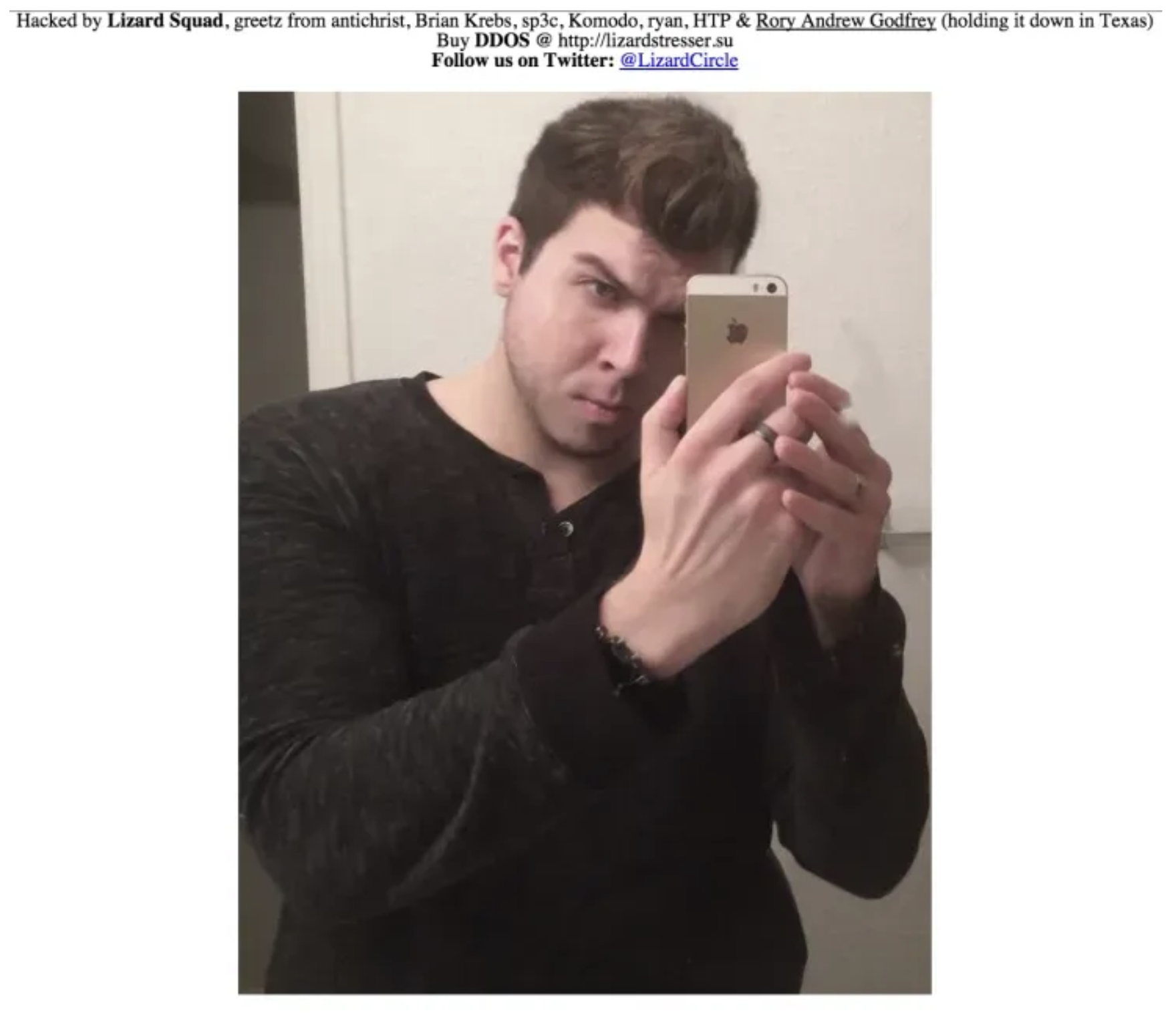
Google.com.vn
In 2015, the domain name for Google’s search engine in Vietnam was briefly hijacked and redirected to a website showing a Caucasian man holding an iPhone promoting cyberattack tools.
Perl.com
The official website for Perl (dedicated to Perl programming, news, and culture) was briefly hacked in 2021 and pointed to a site associated with malware campaigns.
Perl was able to recover the domain after a few months, but the company later explained that the damage had been long-lasting, adding that “various security products had also blacklisted Perl.com and some DNS servers had sinkholed it.”
The Real Consequences of Domain Hijacking Beyond Lost Traffic
Domain hijacking is often described as a traffic problem. In reality, traffic loss is usually the smallest and shortest-lived impact. The deeper consequences linger long after control of the domain is restored.
Trust damage comes first. When a domain is hijacked, attackers often redirect visitors to spam, phishing pages, or malware. Users do not distinguish between a hijacker and the original owner. From their perspective, the domain failed them. That loss of trust is hard to measure and harder to rebuild.
Email breaks quietly and causes collateral damage. Hijackers frequently change DNS records, including MX and TXT entries. Legitimate email stops working or gets flagged as suspicious. Password resets fail. Invoices bounce. Support conversations disappear. Even after recovery, email reputation can take weeks to normalize.
Search visibility takes a hit too. If the domain serves malicious or unrelated content, search engines may deindex it or apply warnings. Cleaning that up involves more than regaining access. It often requires security reviews, reindex requests, and time. Rankings do not snap back instantly.
Security fallout spreads internally. Once a domain is compromised, teams must assume related systems are exposed. API callbacks, OAuth redirects, webhook endpoints, and third-party integrations tied to the domain may all need rotation or revalidation. That creates unplanned work across multiple teams.
Recovery itself is rarely fast. Registrars have different processes and response times. Proving ownership can take days, especially if account access is also compromised. During that window, the hijacker controls the public face of the business.
There are also long-term operational costs. Teams add extra checks, approvals, and manual steps around DNS and registrar access. Some are necessary. Others slow routine work because the incident left scars. This friction shows up months later as slower changes and higher cognitive load.
Monitoring gaps often get exposed. Many teams discover hijacking only after users complain. DNS changes, SSL issues, or unexpected redirects went unnoticed because nothing was watching for them. Post-incident, monitoring usually expands to cover registrar locks, DNS integrity, and certificate changes.
The key takeaway is that domain hijacking is not a one-system failure. It is a control-plane failure that ripples through identity, email, search, and trust. Prevention and early detection cost far less than repairing those downstream effects.
A Few Last Words
Domain hijacking may be an invisible threat but it’s a very real one — but by staying vigilant and employing security best practices, you can protect your digital real estate from falling into the wrong hands.
Essential preventative measures are:
- Crafting strong
- unique passwords
- keeping registration information private
- enabling two-factor authentication
- locking your domain
You should also take advantage of monitoring tools like UptimeRobot to keep an eye on domain expiration so hijackers don’t have a chance to pounce as soon as a domain becomes available.
FAQ’s
What is domain hijacking?
Domain hijacking is when an attacker gains unauthorized control of a domain name. This usually happens by compromising registrar accounts, DNS settings, or transfer authorization. Once hijacked, attackers can redirect traffic, intercept email, or take a site offline.
What are the immediate consequences of domain hijacking?
The most immediate impact is loss of access to your website and email. Traffic may be redirected to malicious sites, phishing pages, or competitors. Recovery can take hours or days, during which users and revenue are affected.
How does domain hijacking affect email and security?
Attackers can change MX, SPF, DKIM, or DMARC records to intercept or spoof email. This can lead to data leaks, phishing campaigns, and blacklisting. Email trust is often harder to restore than website access.
Can domain hijacking cause long-term damage?
Yes. Beyond downtime, hijacking can damage brand reputation, SEO rankings, and customer trust. Search engines may flag the domain as unsafe, and users may hesitate to return even after recovery.
What are the most common causes of domain hijacking?
Common causes include weak registrar passwords, missing two-factor authentication, phishing, and outdated contact information. DNS misconfigurations and expired domains are also frequent entry points. Most hijacks are preventable with basic security hygiene.