Ping is often the first check people run, and the first one they misread. A host replies, yet users report slowness or timeouts. Or ping fails, but the service looks fine. That gap leads to bad assumptions during incidents.
This guide explains what ping actually measures, how ICMP works, and why results don’t always match real user experience. It focuses on the cases that confuse teams most: packet loss, latency spikes, blocked requests, and misleading “up” signals.
You’ll learn how to interpret ping output with context, understand when it helps or misleads, and decide how to use it alongside other checks. If ping is part of your troubleshooting flow, this will make it useful again.
How does ping work
When you execute a ping command, your computer sends a small packet of data to another device on the network. This packet is then echoed back to the originating device, confirming that the network path is functional.
With UptimeRobot, you can get free ping monitoring with 5-minute intervals. Improve your uptime and respond to any incident quickly with live alerts.
During a ping test, Internet Control Message Protocol (ICMP) packets are exchanged. These packets contain essential information such as the source and destination IP addresses and a sequence number to keep track of each packet sent and received.
The round-trip time (RTT) is calculated by measuring the time it takes for the ICMP packet to travel from the source to the destination and back again. This time is recorded in milliseconds and indicates the latency between the two devices.
The ping process involves several stages:
- Packet Generation: Your device generates an ICMP echo request packet.
- Packet Transmission: This packet is sent over the network to the destination device.
- Echo Reply: The destination device receives the packet and responds with an ICMP echo reply.
- Receipt of Reply: Your device receives the echo reply and calculates the RTT.
Ping times can vary depending on the type of network. In wired networks, ping times are usually lower and more consistent due to the stable nature of the physical connections. In wireless networks, factors such as signal interference and distance from the router can cause higher and more variable ping times.
How to use ping in troubleshooting
Ping is an essential tool for identifying network connectivity issues. It works by sending an ICMP echo request to a target host and receiving an echo reply. If the ping succeeds, it confirms that the host is reachable, and the response time gives insight into network performance.
To use ping, simply open the command line on your device and type ping followed by the IP address or domain (e.g., ping google.com or ping 172.168.9.13).
If a ping returns a slow response, it may indicate network congestion or routing problems. When a ping fails, it signals issues such as a host being offline, network interruptions, or incorrect IP addressing. For example, a “Request Timed Out” message could point to a blocked port or firewall restriction.
What is ping spoofing?
Ping spoofing is a network attack where a malicious user sends forged ICMP echo requests (ping packets) to make it appear as if they are coming from a trusted or legitimate source.
This method can be used to hide the attacker’s identity or to flood a network with traffic, causing disruptions. By manipulating the source IP address in the ping request, the attacker can mislead the target and make it harder to trace the origin of the malicious activity.
Ping commands and how to use them
Ping commands allow you to test the reachability of a host and measure the time it takes for packets to travel to the destination and back. Here’s a detailed look at how to use various ping commands, from basic to advanced options.
Basic ping commands
The most fundamental ping command sends an ICMP echo request to a specified host to check availability and measure response times. The syntax for this command is straightforward:
Ping Command:
ping [hostname or IP address]You can control the number of ping requests sent to a host using specific options. This is useful for testing consistency and network stability over multiple packets.
Unix/Linux:
ping -c 4 [hostname or IP address]Windows:
ping -n 4 [hostname or IP address]In these examples, the -c or -n option tells the command to send four ping requests to the specified host.
Advanced ping command options
Ping commands offer several advanced options to refine your network diagnostics. Here are some useful ones:
Timeout
Set a timeout for each ping request to ensure the test doesn’t hang indefinitely if there is no response.
Unix/Linux:
ping -W 2 [hostname]Windows:
ping -w 2 [hostname]This sets a timeout of 2 seconds for each ping response.
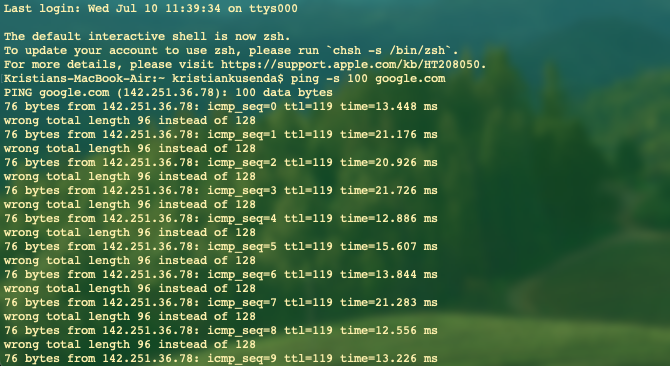
Packet Size
Change the size of the packet sent to test how the network handles different payload sizes.
Unix/Linux:
ping -s 100 [hostname]Windows:
ping -l 100 [hostname]This sets the packet size to 100 bytes.
Flood Ping
Flood ping sends packets as quickly as possible to stress-test the network. Use with caution, as it can overwhelm the network.
Unix/Linux:
ping -f [hostname]This option is not typically available on Windows systems due to its potential to cause network disruption.
Summary of Ping Commands
| Command | Description | Unix/Linux Example | Windows Example |
| Basic Ping | Sends an ICMP echo request to a host | ping [hostname or IP address] | ping [hostname or IP address] |
| Number of Requests | Specifies the number of ping requests to send | ping -c 4 [hostname or IP address] | ping -n 4 [hostname or IP address] |
| Timeout | Sets a timeout for each ping request | ping -W 2 [hostname] | ping -w 2 [hostname] |
| Packet Size | Changes the size of the packet sent | ping -s 100 [hostname] | ping -l 100 [hostname] |
| Flood Ping | Sends packets as quickly as possible (Unix/Linux) | ping -f [hostname] | Not typically available |
How to run a ping test
Running a ping test is a straightforward yet powerful way to diagnose and understand your network’s performance. According to Kristian Razum, DevOps Specialist, you “open up the command prompt (Windows) or terminal (Linux/Mac) and simply type ping – followed by destination DNS / IPv4 address.”
Here’s a more detailed step-by-step description of the process:
1. Open Command Prompt or Terminal: The first step in running a ping test is to open the command line interface. On Windows, you can open Command Prompt by searching for “cmd” in the Start menu. On macOS or Linux, open Terminal from your applications menu.
2. Type the Ping Command: Once you have the Command Prompt or Terminal open, type the ping command followed by the hostname or IP address of the target device. For example:
ping example.comThis command sends an ICMP echo request to the specified host and waits for a reply.
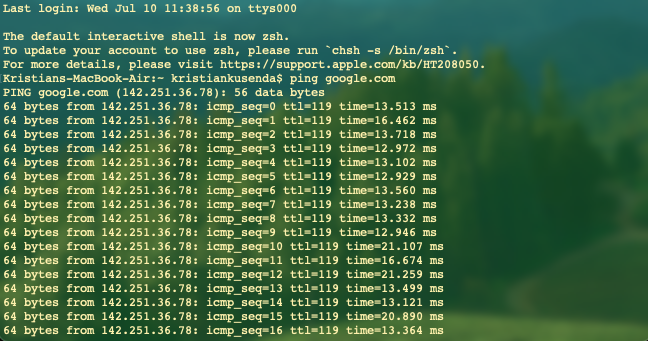
3. Analyze the Results: After executing the ping command, you will receive a series of responses from the target device. These responses will include information such as the number of packets sent and received, round-trip time (RTT), and any packet loss. By analyzing these results, you can gauge the health and performance of your network connection.
Common parameters for a ping test
You can adjust the size of the packets sent during the ping test using the -s option on Unix/Linux systems or the -l option on Windows systems. For example:
ping -s 100 example.com # Unix/Linuxping -l 100 example.com # WindowsThis sets the packet size to 100 bytes, allowing you to test how the network handles different payload sizes.
Timeout: To set a timeout for each ping request, use the -W option on Unix/Linux systems or the -w option on Windows systems. For example:
ping -W 2 example.com # Unix/Linuxping -w 2 example.com # WindowsThis command sets a timeout of 2 seconds for each ping response, ensuring the test doesn’t hang indefinitely if there is no reply.
✔️One of the most common mistakes when running a ping test is using an incorrect hostname or IP address. Always double-check the address to ensure it’s accurate.
✔️If your pings fail, it might be due to network configuration issues. Ensure that your network settings are correctly configured and that no firewall rules are blocking ICMP packets.
Interpreting ping test results
The round-trip time (RTT) values indicate the time it takes for a packet to travel from your device to the target and back again. Low RTT values suggest good connectivity, while high RTT values can indicate latency issues. For instance, an RTT of less than 50 milliseconds is generally considered excellent, while anything above 200 milliseconds might indicate a problem.
Packet loss is another critical metric to monitor. It represents the number of packets sent that did not receive a reply. Any packet loss is a sign of network issues, such as congestion or faulty hardware. For example, 0% packet loss indicates a healthy network, whereas any packet loss percentage suggests that there are problems that need to be addressed.
Most importantly we should check if we got a reply from the target we are pinging. If we see ‘Reply from,’ it means that the target host is alive and replying to our ICMP request. The second most important thing in this request is the ‘time’ – this shows us how long it took for the packet to travel from us to the destination, and back to us.
What impacts ping and ways to improve it
Several factors can influence ping times, leading to increased latency and slower network performance. Understanding these factors can help you take steps to optimize your network.
Network Congestion: High traffic on a network can significantly slow down responses. When multiple devices are using the same network, the data packets must compete for bandwidth, leading to delays. This is especially common during peak usage times, such as in the evening when many users are streaming videos or gaming.
Physical Distance: “The longer the distance, the higher the latency because of the distance the data package has to travel in the optical cable,” says Razum. This is because the packets must pass through more routers and switches, each introducing a small delay. For example, pinging a server located on another continent will typically result in higher ping times compared to a server in the same city.
Interference: In wireless networks, interference from other electronic devices, physical obstructions like walls, and competing Wi-Fi networks can cause delays. Wireless signals can be disrupted or weakened, leading to increased ping times and packet loss.
Best practices for improving ping times
Improving ping times involves optimizing your network and minimizing the factors that cause delays. Here are some best practices:
| Factor | Impact on Ping | Improvement Strategy |
| Network Congestion | Slows down responses during high-traffic periods | Ensure network settings are optimized for performance and configure QoS settings to prioritize important traffic. Implement bandwidth management techniques to distribute network resources more effectively. |
| Physical Distance | Increases RTT with greater distances | Choose servers that are geographically closer to you to reduce RTT. Use Content Delivery Networks (CDNs) to cache content closer to your location. Optimize routing paths through your Internet Service Provider (ISP) for more efficient data travel. |
| Interference | Causes delays in wireless networks | Wired connections offer lower latency and more stable performance compared to wireless connections. Use Ethernet cables to connect devices, especially for activities requiring low ping times, such as online gaming or video conferencing. |
Whether you’re gaming, video conferencing, or simply browsing, optimizing your ping can make all the difference.
What Ping Can and Cannot Tell You About System Health
Ping is often the first tool people reach for because it is simple and fast. It answers one narrow question: can this host respond to network requests right now? That clarity is useful, but only if you understand the limits.
At a basic level, ping checks reachability and round-trip latency. If packets come back, the host is reachable. If latency spikes, something along the network path is slowing down. This makes ping good for spotting network outages, routing issues, or hosts that have dropped off the map.
What ping does not tell you is just as important. A successful ping does not mean the service is working. The web server can be down, the database unreachable, or the app returning errors while ping still looks healthy. ICMP replies only prove the machine answers at the network layer.
Firewalls and security rules complicate things further. Many systems block ICMP entirely. In those cases, failed pings do not mean downtime. They mean ping is not allowed. This is why ping results need context before triggering alerts.
Latency trends are where ping adds longer-term value. A gradual increase in response time often points to congestion, resource pressure, or routing changes. These slowdowns usually appear before full outages. Tracking averages and percentiles matters more than single spikes.
Ping also lacks user perspective. It cannot show regional differences unless checks run from multiple locations. A host may respond quickly from one network while timing out from another. Single-source ping checks miss that class of problem.
Because of these limits, ping works best as a baseline signal. It tells you when a host disappears or the network degrades. It should not be your only check for user-facing systems.
Pair ping with higher-level monitoring. HTTP checks validate application responses. Heartbeat monitors confirm background jobs run. Together, they answer not just “is the host up,” but “does the system actually work.”
Ping is simple by design. Use it for what it is good at, and do not ask it to explain failures it cannot see.
Conclusion
Ping is a useful tool, but only when you understand what it is actually telling you.
It measures reachability and basic network latency, not application health or user experience. A successful ping does not mean your service is working. A failed ping does not always mean your system is down. Without context, ping results can lead teams to the wrong conclusions during incidents.
Used correctly, ping is a baseline signal. It helps detect network outages, routing problems, and rising latency trends that often appear before larger failures. Its real value comes from patterns over time, not single responses, and from being combined with other checks that validate what users actually depend on.
The key is knowing its limits. Ping should answer “can this host be reached right now,” not “is everything working.” Pair it with HTTP monitoring, application checks, and regional probes to get a complete picture of system health.
Ping becomes powerful again when it is treated as one piece of evidence, not the verdict.
FAQ's
-
Ping tests whether a host is reachable on the network and how long it takes to respond. It sends ICMP echo requests and waits for replies. If there’s no response, the host or network path may be unreachable.
-
No, it only means the host responds at the network level. Applications like web servers or databases can still be down even if ping succeeds. Ping confirms connectivity, not application health.
-
Ping can fail if ICMP traffic is blocked or rate-limited by firewalls, cloud providers, or routers. Many production systems intentionally disable ping for security reasons. In those cases, higher-level checks are more reliable.
-
Ping time (latency) shows how long packets take to travel to the host and back. Packet loss indicates dropped packets along the path, which can signal network congestion or instability. Rising latency or loss often precedes outages.
-
Ping checks reachability and response time to a single host. Traceroute shows the network path taken to reach that host, hop by hop. Traceroute is better for diagnosing where delays or drops occur.