Incidents rarely give you time to think. An alert fires, users complain, and teams scramble to decide who owns what and what to do next. Without a clear response plan, confusion becomes the biggest source of downtime.
This guide breaks incident response planning down to how it works in practice. It’s based on common failure points teams hit during real outages: unclear roles, missing runbooks, slow escalation, and poor handoffs under pressure.
You’ll learn how to build an incident response plan that’s easy to follow when things go wrong, test it before you need it, and use it to reduce recovery time. If outages still feel chaotic, this is where structure starts.
We’ll cover the following topics, and by the end, you’ll be fully equipped to create your own rock-solid IRP.
- What is an incident response plan?
- Why you need an IRP
- Steps to creating an IRP
- Preparation
- Detection and analysis
- Containment
- Eradication & recovery
- Post-incident activity
- Common mistakes in incident response planning
- Real-world examples
- Tools and resources
- IRP checklist
- Conclusion
What is an Incident Response Plan?
An Incident Response Plan (IRP) is a structured strategy designed to help organizations detect, respond to, and recover from cybersecurity incidents.
It acts as a clear roadmap for IT teams to follow when dealing with threats like data breaches, malware attacks, system failures, or insider threats.
Key objectives of an IRP
A well-designed IRP serves several purposes:
Minimize damage: Contain threats quickly to reduce financial and operational impact.
Restore operations efficiently: Guarantees a faster recovery and minimizes downtime.
Regulatory compliance: Meet cybersecurity standards like GDPR, HIPAA, or PCI-DSS.
Improve response coordination: Clearly define roles and responsibilities to avoid confusion during a crisis.
Reduce future risks: Identify security gaps and refine security policies based on lessons learned.
How does an IRP fit into a cybersecurity strategy?
An Incident Response Plan is vital to an organization’s broader cybersecurity framework.
It works alongside:
- Risk management policies: Identifying and mitigating potential threats before they happen.
- Security tools and monitoring systems: Detecting anomalies in real time (like SIEM, IDS).
- Disaster recovery and business continuity plans: Providing quick recovery from major security events.
An IRP is a bit like the fire drill in the cybersecurity world, acting as a step-by-step guide that ensures your team knows exactly what to do when a crisis hits.
Why is an Incident Response Plan important?
Cybersecurity incidents are no longer a question of if they will happen, but when. Without a structured response plan, organizations risk financial losses, reputational damage, and regulatory penalties.
A well-prepared Incident Response Plan (IRP) ensures that when a breach or cyberattack happens, there is a clear plan of action in place to mitigate damage and restore operations as quickly as possible.
The risks of not having an IRP
Organizations without a proper IRP often struggle with the following:
- Extended downtime: Unstructured responses lead to longer disruptions.
- Higher costs: The average cost of a data breach in 2023 was $4.45 million, according to IBM.
- Regulatory penalties: Non-compliance with cybersecurity regulations like GDPR, HIPAA, or PCI-DSS can result in fines and legal consequences.
- Loss of customer trust: A slow or ineffective response can erode brand reputation and customer confidence.
How an IRP supports compliance requirements
Many industries are required by law to have an IRP in place. Some key regulations include:
- GDPR (General Data Protection Regulation): Requires organizations to notify authorities and affected individuals within 72 hours of a data breach.
- HIPAA (Health Insurance Portability and Accountability Act): Mandates a formal incident response process for protecting patient data.
- PCI-DSS (Payment Card Industry Data Security Standard): Enforces strict security measures for handling payment card information.
Failing to comply with these regulations can lead to hefty fines and legal repercussions. An IRP ensures that organizations respond swiftly and within legal guidelines.
Incident response and organizational resilience
Cybersecurity threats are inevitable, but how an organization prepares and responds determines its resilience. A well-structured IRP:
- Reduces operational impact by limiting damage and downtime.
- Increases employee preparedness through clear protocols and interactive training.
- Improves cybersecurity posture by continuously refining security measures based on past incidents.
Knowing the importance of an IRP, let’s start going through how to make one to protect your business and your data.
Steps to creating an Incident Response Plan
Creating an effective Incident Response Plan requires a structured approach that allows for quick detection, containment, and resolution of security incidents.
A well-designed IRP outlines who does what, when, and how in response to cyber threats, minimizing disruption and financial impact.
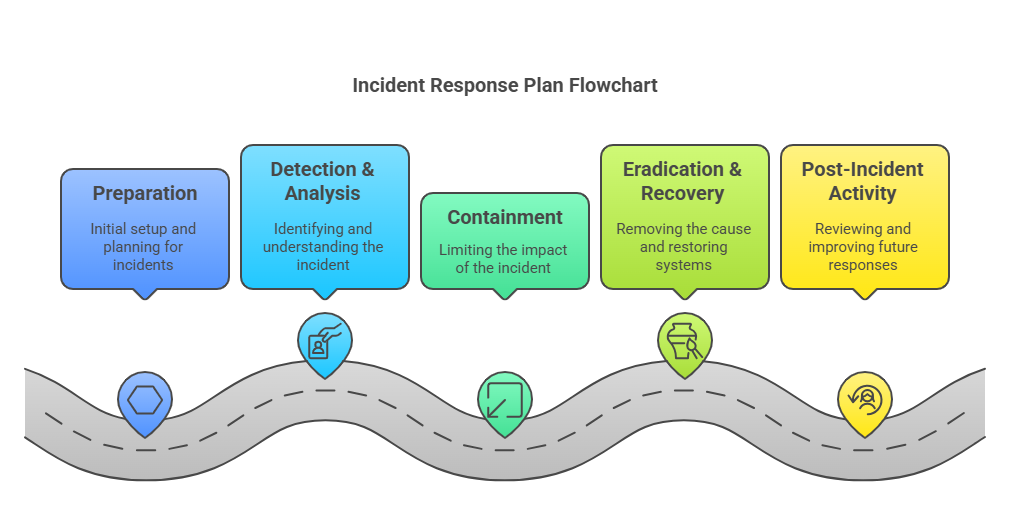
Now, let’s break down each step in detail.
1. Preparation
The best way to handle a security incident is to prepare for it before it happens. This phase focuses on establishing policies, training teams, and setting up communication protocols to ensure a swift response when a threat arises.
Building a cross-functional Incident Response Team
Every organization should designate an Incident Response Team (IRT) that includes members from different departments:
| Role | Responsibility |
| Incident Manager | Oversees the response process and ensures coordination. |
| IT Security Lead | Analyzes security threats and determines containment actions. |
| Communications Lead | Handles internal and external communication about the incident. |
| Legal & Compliance | Makes sure response actions meet regulatory requirements. |
| Business Continuity | Coordinates recovery efforts to restore normal operations. |
Defining these roles before an incident occurs allows your team to react immediately and effectively when a threat is detected.
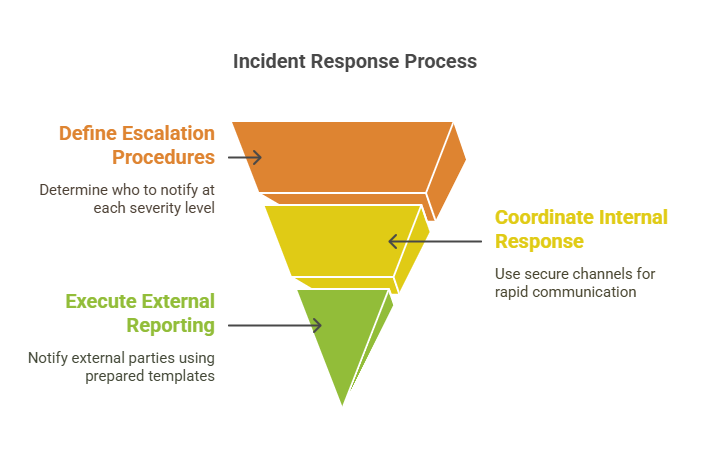
Setting up communication protocols
Clear communication is of the utmost importance during a cyber incident. Organizations should establish:
- Escalation procedures: Define who needs to be notified at each severity level.
- Internal response channels: Use secure messaging platforms for rapid coordination.
- External reporting protocols: Have templates ready for notifying law enforcement, regulators, and customers/media if required.
An organization-wide incident communication plan keeps information flowing without delays or misinformation, and sets your team up for success.
2. Detection and analysis
Once an incident occurs, the speed and accuracy of detection determine how much damage is prevented.
The faster a threat is identified, the quicker containment and resolution can begin.
This phase focuses on detecting security threats, classifying their severity, and analyzing their potential impact.
Identifying and classifying threats
Security incidents come in many forms, and not all require the same level of response. A well-defined classification system helps your team prioritize threats with ease.
| Incident Type | Example Scenarios | Severity Level |
| Data Breach | Unauthorized access to sensitive customer data | High |
| Malware Attack | Ransomware infection disrupting systems | High |
| DDoS Attack | Website or network overloaded with malicious traffic | Medium |
| Insider Threat | Employee stealing or leaking company data | Medium |
| Phishing Attack | Fake emails tricking employees into sharing credentials | Low to Medium |
Note that the severity levels of these incidents vary from company to company.
The role of monitoring and detection tools
Organizations rely on advanced security tools to detect threats in real time. These tools provide automated alerts, reducing the time it takes to respond.
Key detection tools & technologies
- SIEM (Security Information & Event Management): Collects and analyzes security logs to detect anomalies.
- IDS/IPS (Intrusion Detection/Prevention Systems): Identifies and blocks suspicious activity in real-time.
- Threat intelligence platforms: Uses external data sources to detect known attack patterns.
- Endpoint detection & response (EDR): Monitors activity on individual devices for early signs of compromise.
A combination of these tools gives a strong security posture that detects both known and emerging threats.
Incident detection with UptimeRobot
While traditional security tools focus on network and endpoint security, proactive monitoring of system uptime and service availability is just as essential for detecting potential threats.
UptimeRobot provides real-time website and server monitoring, helping to detect and respond to unexpected downtime, performance issues, or service disruptions.
By integrating UptimeRobot’s automated alerts into an incident response plan, organizations can:
Detect anomalies faster: Identify unexpected downtime or performance degradation that could indicate a cyberattack.
Reduce response times: Receive instant notifications about system failures before they escalate.
Build a stronger security posture: Combine uptime monitoring with your chosen SIEM, IDS, and other security tools for a more comprehensive incident response strategy.
Tip: Security isn’t just about preventing breaches – it’s also about having stronger system reliability and more uptime. Pairing cybersecurity tools with UptimeRobot’s monitoring capabilities can provide an early warning system for potential threats.
Start monitoring critical services today with UptimeRobot and strengthen your security framework.
Quick analysis of incidents
Once a security alert is triggered, teams must assess the situation quickly to decide the next steps. A standardized analysis process ensures consistency and efficiency.
Rapid incident assessment checklist
- What happened? Identify the type of security event.
- When was it detected? Determine how long the threat has been active.
- What systems are affected? Identify impacted servers, networks, or databases.
- Who is involved? Determine if the incident involves external attackers or insider threats.
- What is the potential impact? Estimate the risk to operations, finances, and reputation.
3. Containment
Once a security incident is detected, the first priority is containment – preventing the attack from spreading, and limiting further damage.
A well-defined containment strategy empowers teams to have a swift and effective response based on the severity of the incident.
Immediate actions to contain threats
Containment measures should align with the nature of the attack and the affected systems. Quick decision-making can reduce damage and buy time for a full investigation.
| Containment strategy | Use case | Timeframe |
| Isolating affected systems | Disconnecting infected servers or compromised endpoints | Immediate |
| Blocking malicious IPs and accounts | Preventing further unauthorized access | Immediate |
| Disabling compromised credentials | Resetting passwords for compromised user accounts | Short-term |
| Segmenting the network | Restricting access to sensitive areas to contain the breach | Short-term |
| Patching vulnerabilities | Updating software to prevent reinfection | Long-term |
Tip: Effective containment prevents further escalation while allowing security teams to analyze the root cause and plan the next steps.
4. Eradication & recovery
Once the attack is contained, teams must remove the root cause to prevent recurrence.
- Remove malware or malicious code: Scan systems for trojans, viruses, or ransomware and eliminate them.
- Identify and close security gaps: Fix vulnerabilities that attackers exploited, such as weak passwords or outdated software.
- Rebuild or restore affected systems: If necessary, reinstall compromised servers or roll back to a clean backup.
Thorough eradication guarantees that attackers can’t regain access or exploit the same weaknesses again.
Recovering operations
With the threat removed, the focus shifts to restoring business functions safely. The goal is to resume normal operations with minimal disruption while keeping systems secure.
- Verify integrity of data and systems: Confirm that restored systems are free from compromise.
- Gradually reconnect affected systems: Avoid reintroducing vulnerabilities by monitoring closely after restoring services.
- Monitor for signs of reinfection: Use security tools to detect lingering threats or suspicious activity.
- Communicate with stakeholders: Notify leadership, customers, and regulatory bodies as needed.
5. Post-incident activity
Once an incident has been contained and systems have been restored, the work isn’t over yet. The final step in the Incident Response Plan (IRP) is to analyze what happened, refine the response strategy, and improve cybersecurity measures to prevent future incidents.
Conducting a post-mortem analysis
A post-incident review is necessary for understanding what went wrong and how to strengthen defenses moving forward. This review should be conducted as soon as possible after recovery while the details are still fresh.
Key questions for post-incident analysis
- How was the incident detected? Did security tools or employees identify the issue?
- What was the root cause? Was it a vulnerability, human error, or insider threat?
- How effective was the response? Were containment and recovery efforts timely?
- What delays or challenges occurred? Did poor communication or lack of resources slow the response?
- What improvements can be made? Are there tools, training, or processes that need updating?
Organizations should document findings in an incident report that can be used to refine future responses.
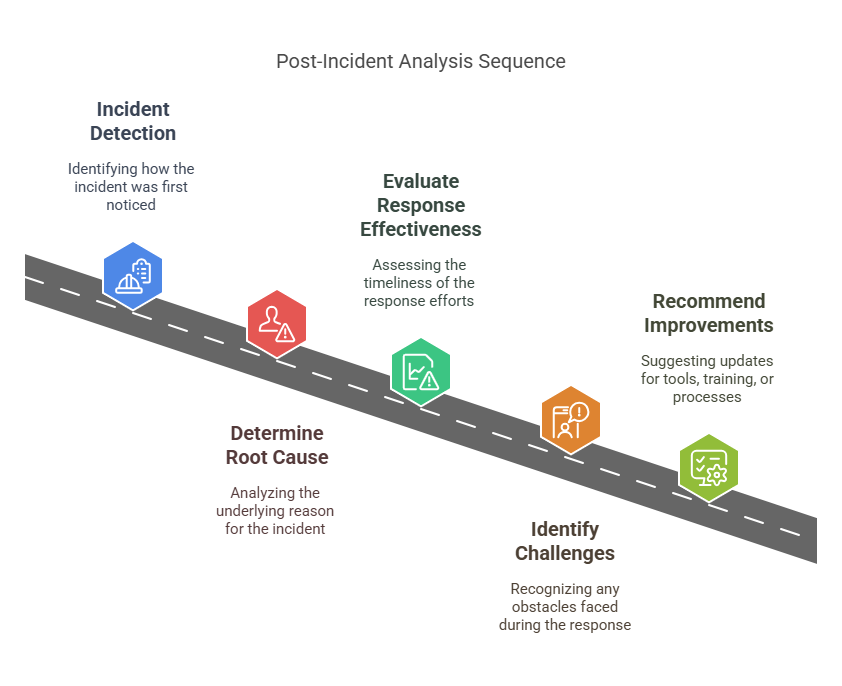
Updating the Incident Response Plan
An IRP is not a one-time document – it should evolve based on new threats, emerging technologies, and past experiences. After a post-mortem, organizations should:
- Update response playbooks: Adjust procedures to reflect lessons learned.
- Refine security policies: Implement new controls to reduce the risk of recurrence.
- Improve automation: Identify opportunities to use AI-powered threat detection or response orchestration tools.
Training and regular drills for employees
Even the best IRP is useless if employees don’t know how to follow it. Regular training and simulated cyberattack exercises help teams stay prepared and respond efficiently.
- Tabletop exercises: Run through hypothetical scenarios to practice decision-making.
- Live attack simulations: Conduct penetration testing or red team exercises.
- Phishing awareness programs: Educate employees on recognizing phishing attempts.
A well-trained workforce reduces response time and minimizes mistakes during real incidents.
Common mistakes in incident response planning
Even organizations with a well-documented IRP can fall victim to avoidable mistakes that weaken their ability to handle security incidents. Below are some of the most common pitfalls and how to prevent them.
1. Failure to regularly update the IRP
A static IRP quickly becomes outdated and ineffective. Cyber threats evolve rapidly, and response strategies must keep pace.
Why it’s a problem:
- New attack methods (like AI-driven phishing or ransomware-as-a-service) may bypass existing defenses.
- Staff changes can leave critical roles unfilled if the IRP isn’t updated with new personnel.
- Compliance requirements (GDPR, HIPAA, PCI-DSS) frequently change, and an outdated IRP may lead to regulatory violations.
How to prevent it:
- Review and update the IRP quarterly or after major incidents.
- Incorporate recent threat intelligence into response strategies.
- Make sure all team members are aware of updates and trained accordingly.
2. Neglecting emerging threats like ransomware
Ransomware attacks have surged in recent years, yet many organizations lack specific response plans to handle them effectively.
Why it’s a problem:
- Traditional incident response plans may not account for ransom demands or data recovery challenges.
- Without a solid backup and recovery strategy, businesses risk permanent data loss.
- Delayed response can lead to longer downtimes and financial losses.
How to prevent it:
- Create a dedicated ransomware response protocol within the IRP.
- Regularly test data backups and ensure they are stored securely off-network using scalable backup storage.
- Simulate ransomware attack scenarios to prepare teams for real-life incidents.
3. Poor communication during incidents
A lack of clear communication can cause confusion, delays, and misinformation, making an already bad situation worse.
Why it’s a problem:
- If IT and executive leadership aren’t aligned, decision-making slows down.
- Employees may unknowingly escalate an attack if they don’t know how to report threats.
- Customers and stakeholders may lose trust if communication about an incident is mishandled.
How to prevent it:
- Establish predefined escalation and notification procedures.
- Use secure internal communication channels for incident response coordination.
- Train employees on when and how to report suspicious activity.
4. Inadequate training of staff
An IRP is only as effective as the people executing it. If employees don’t know their roles or lack cybersecurity awareness, response efforts can fall apart in critical moments.
Why it’s a problem:
- Employees may hesitate or make critical mistakes when responding to threats.
- IT and security teams may lack hands-on experience with real-world attack scenarios.
- Compliance audits may fail if organizations can’t demonstrate proper security training.
How to prevent it:
- Conduct regular incident response drills and tabletop exercises.
- Provide ongoing security awareness training for all employees.
- Ensure new hires are educated on cybersecurity best practices.
Real-world examples and case studies
Understanding how organizations have navigated cybersecurity incidents provides a real look into effective incident response planning. These are some notable examples that highlight the importance of a well-structured Incident Response Plan (IRP).
1. The Target Data Breach (2013)
In 2013, retail giant Target experienced a significant data breach that compromised the personal and credit/debit card information of over 70 million customers.
Incident response
Upon discovering the breach, Target’s incident response included:
- Engaging law enforcement: Collaborated with federal agencies to investigate the breach.
- Hiring third-party forensics: Brought in cybersecurity experts to identify the breach’s origin and scope.
- Customer communication: Notified affected customers and offered free credit monitoring services.
Lessons learned
Though this was undoubtedly a nightmare for Target, some valuable lessons were learned along the way:
- Early detection is crucial: Implementing advanced monitoring systems could have identified the breach sooner.
- Third-party vendor management: The breach originated through a third-party HVAC vendor, underscoring the need for stringent security measures for vendors.
- Transparent communication: Prompt and clear communication helped mitigate reputational damage.
2. The WannaCry Ransomware Attack (2017)
In May of 2017, the WannaCry ransomware attack affected over 300,000 computers across 150 countries, targeting entities like hospitals, banks, and telecommunications.
Incident response
Organizations responded by:
- Deploying security patches: Applied patches to address the exploited vulnerability in Windows systems.
- Isolating infected systems: Disconnected affected systems to prevent further spread.
- Restoring from backups: Used clean backups to restore data without paying the ransom.
Lessons learned
This devastating attack brought light to some glaring issues in the cybersecurity community and left us with these lessons:
- Regular updates: Maintaining up-to-date systems is vital to prevent exploitation.
- Backup strategies: Regular backups are essential for data recovery without succumbing to ransom demands.
- Global collaboration: The attack highlighted the need for international cooperation in cybersecurity.
3. The SingHealth Data Breach (2018)
Singapore’s largest healthcare group, SingHealth, suffered a cyberattack in 2018, resulting in the theft of personal data from 1.5 million patients, including the Prime Minister, Lee Hsien Loong.
Incident response
The response involved:
- System isolation: Disconnected affected systems to contain the breach.
- Enhanced monitoring: Implemented additional system monitoring and controls.
- Policy review: Conducted a comprehensive review of cybersecurity policies and postponed certain initiatives for reassessment.
Lessons learned
Organizations can apply these takeaways to enhance their own security measures:
- Proactive monitoring: Continuous system monitoring can aid in early detection.
- Policy adaptation: Regularly updating cybersecurity policies is critical to addressing evolving threats.
- Public communication: Transparent communication with the public helps maintain trust.
Organizations that analyze these real-world incidents can improve their cybersecurity defenses, adapt to emerging threats, and build stronger resilience against future attacks.
Tools and resources for incident response
Without the proper technology and support, teams may struggle to respond efficiently, increasing the risk of damage.
This section outlines the most valuable tools and resources that organizations can use to strengthen their incident response capabilities.
Key tools
Different tools serve different functions within an incident response strategy. Below is an overview of the most essential categories:
| Tool Type | Purpose | Examples |
| SIEM (Security Information and Event Management) | Collects and analyzes security logs to detect threats in real time | Splunk, IBM QRadar, LogRhythm |
| EDR (Endpoint Detection and Response) | Monitors and responds to threats on endpoint devices | CrowdStrike, SentinelOne, Microsoft Defender for Endpoint |
| Intrusion Detection/Prevention Systems (IDS/IPS) | Detects and blocks malicious activity on a network | Snort, Suricata, Palo Alto Networks |
| Threat Intelligence Platforms | Provides real-time threat data and analysis | Recorded Future, ThreatConnect, Anomali |
| Forensic Analysis Tools | Helps investigate security breaches and collect digital evidence | Autopsy, EnCase, FTK (Forensic Toolkit) |
| Incident Response Automation | Automates incident response workflows to reduce response time | SOAR (Security Orchestration, Automation, and Response) platforms like Palo Alto Cortex XSOAR and Splunk Phantom |
- Faster detection: SIEM and EDR tools provide real-time alerts on suspicious activity.
- Stronger containment: IDS/IPS prevent attacks from spreading across networks.
- Better decision-making: Threat intelligence platforms help teams understand emerging threats.
- More efficient response: Automated response tools allow teams to act faster and reduce human error.
Using UptimeRobot for incident response
With real-time monitoring and automated alerts, IT teams can react faster to disruptions, whether they stem from server failures, performance degradation, or potential security threats.
- Real-time monitoring: Instantly detects downtime, latency issues, and service disruptions.
- Automated notifications: Alerts IT teams via SMS, email, Slack, and other channels to enable a rapid response.
- Performance tracking: Identifies unusual spikes, slowdowns, or anomalies that may indicate an attack.
- API integrations: Seamlessly connects with security tools, SIEM platforms, and incident response workflows.
Unplanned downtime and security incidents can cripple operations. UptimeRobot provides the proactive monitoring your organization needs to detect, respond to, and recover from disruptions faster.
Start monitoring with UptimeRobot today and keep your critical services running smoothly.
Recommended resources for building an IRP
Organizations looking to improve or build their IRP can benefit from industry frameworks, guidelines, and templates. Here are some of the best resources available:
- NIST Cybersecurity Framework: A comprehensive guide to security incident response planning
- SANS Incident Handler’s Handbook: A practical resource for handling and responding to security incidents
- MITRE ATT&CK Framework: A globally accessible knowledge base of tactics and techniques used by attackers
- CIS Controls: Best practices for securing IT systems and responding to incidents
With these tools and resources, businesses can greatly improve their incident response capabilities, reduce risk exposure, and maintain operational resilience in the face of cyber threats.
Checklist for Incident Response Plans
A well-structured IRP is only effective when regularly tested, updated, and executed properly. That’s where a thorough checklist comes in handy.
Looking for a quick way to improve your IRP? Download our free IRP checklist template to strengthen your response strategy and minimize downtime in the face of cyber threats.
No email or registration required.
Why an incident response plan only works if it is boring
Incident response plans often fail for one reason: they look good on paper but collapse under pressure. The most effective plans are not clever or exhaustive. They are predictable, short, and easy to follow when people are stressed.
A usable plan starts with clear triggers. Teams need to know exactly when an incident response begins. Vague language like “major issues” leads to hesitation. Specific signals, such as sustained errors, missed jobs, or customer impact, remove debate and save time.
Roles matter more than steps. Someone must coordinate, someone must fix, and someone must communicate. These roles should be assigned by default, not negotiated mid-incident. When everyone knows their lane, response speeds up and confusion drops.
Communication flow is another common failure point. Internal coordination and external updates serve different audiences. Mixing them creates noise. A good plan defines where responders talk, where decisions are recorded, and how users get updates, without overlap.
The plan should also slow teams down in the right moments. Many incidents get worse because changes continue unchecked. A clear deploy freeze or change pause reduces blast radius and prevents accidental escalation while systems are unstable.
Decision guidance beats detailed instructions. No plan can predict every failure mode. Instead of long runbooks, include guardrails. Examples include when to roll back, when to fail over, and when to escalate. These prompts help teams act without waiting for permission.
Testing is what keeps the plan alive. If the plan has never been used, it will not work when needed. Tabletop exercises and lightweight drills expose gaps early and normalize the process. Teams that practice respond more calmly when incidents are real.
After the incident, the plan should guide learning. Post-incident reviews are part of response, not an optional extra. The goal is to adjust systems and process, not to document heroics or assign blame.
A good incident response plan fades into the background. People follow it without thinking. That boredom is a feature, not a flaw.
Conclusion
Cybersecurity incidents are no longer a question of if but when. Without a well-defined Incident Response Plan (IRP), organizations risk prolonged downtime, financial losses, regulatory penalties, and reputational damage.
A strong IRP helps businesses:
- Detect and respond to threats faster, minimizing damage
- Ensure compliance with industry regulations like GDPR, HIPAA, and PCI-DSS
- Improve coordination between IT, security, and leadership teams
- Refine security measures based on lessons learned from past incidents
To stay ahead of evolving cyber threats, businesses should regularly update their IRP, conduct training exercises, and invest in the right monitoring and response tools.
If your organization hasn’t developed a response plan yet, now is the time! Start by assessing your current security posture, assembling an incident response team, and integrating tools like UptimeRobot to monitor critical systems in real time.
The faster you can detect, contain, and recover from an incident, the better your business will withstand cyber threats and maintain operational resilience.
FAQ's
-
An incident response plan is a documented set of steps for detecting, responding to, and recovering from incidents. It defines who does what, when, and how during an outage or security event. The goal is faster, calmer recovery with less user impact.
-
Without a plan, teams waste time deciding roles and next steps during an incident. This increases downtime and confusion. A clear plan reduces decision fatigue and speeds up resolution.
-
At minimum, it should include incident severity levels, roles and responsibilities, communication steps, and escalation paths. It should also define how incidents are detected and how recovery is confirmed. Keep it concise and actionable.
-
On-call engineers or SREs are primary responders. Depending on severity, support, product, or leadership may be involved for communication and decision-making. Roles should be explicit to avoid overlap or gaps.
-
It should be detailed enough to guide action, but not so detailed that it’s hard to follow under pressure. Checklists and decision trees work better than long documents. Clarity beats completeness during incidents.