Port monitoring sounds simple until a service half-fails. The host responds, uptime looks fine, yet a specific port stops accepting connections or times out under load. When that happens, users see errors while monitoring stays quiet.
This guide explains port monitoring in operational terms. It covers what port checks actually test, which failures they catch, and where they fall short compared to deeper service validation. The focus is on how ports behave in real infrastructure, not textbook networking.
You’ll learn when port monitoring is the right signal, how to interpret failures, and how to use it alongside other checks for faster diagnosis. If services depend on open ports, this is how to watch them properly.
Key takeaways
- Ports are critical endpoints that manage the flow of data in and out of your network.
- TCP and UDP are the main transport protocols that use ports to direct traffic.
- Common ports, such as 80 (HTTP), 443 (HTTPS), and 22 (SSH), are frequently monitored because they support vital services.
- Port monitoring helps detect issues early, such as dropped packets, failed connections, or misconfigured devices.
- Monitoring ports provides deeper insight into performance, traffic load, potential security risks, and network health.
- Tools like UptimeRobot make port monitoring simple, providing real-time alerts so you can quickly resolve issues and prevent downtime.
What is a port?
A port can refer to either a physical interface or a virtual communication point, depending on the context. We’ll only focus on virtual ports in this article, but let’s first define both types.
- Physical ports are the openings on devices, such as computers, routers, or servers, that allow connections to peripherals. These connections include USB ports for keyboards and mice, HDMI ports for displays, and Ethernet ports for network cables.
- A virtual port is a logical point in computer networking where data connections start or end. These ports direct network traffic to the correct application or service running on a device.
Difference between UDP and TCP ports
In the Open Systems Interconnection (OSI) model, ports are part of Layer 4, the Transport Layer. Only transport protocols – mainly Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) – can specify which port a data packet should be delivered to. While TCP and UDP both use port numbers to facilitate this, they function quite differently in terms of reliability, speed, and typical use cases.
TCP ports are associated with a connection-oriented protocol, meaning a reliable connection is established before data transmission begins. TCP ensures that all packets arrive in order, without errors, and resends any that are lost along the way. This makes TCP ideal for applications where accuracy and reliability are critical, such as web browsing, email, and file transfers.
UDP ports, on the other hand, are used with a connectionless protocol. UDP sends data without establishing a connection and does not check whether the packets arrive or in what order. While this makes UDP less reliable than TCP, it also reduces overhead, resulting in faster communication. As a result, UDP is preferred for real-time applications like video streaming, online gaming, VoIP, and DNS lookups, where speed is more important than perfect accuracy.
From a port monitoring perspective, TCP ports are easier to track and manage due to their stateful nature. Monitoring tools can easily determine if a TCP port is open, closed, or listening. UDP ports are trickier to monitor because they don’t maintain a persistent connection, requiring more advanced techniques to identify suspicious or unwanted traffic.
| Feature | TCP port | UDP port |
| Protocol type | Connection-oriented | Connectionless |
| Reliability | High, ensures delivery and order | Low, no guarantee of delivery or order |
| Speed | Slower due to overhead | Faster with less overhead |
| Connection state | Maintains connection state | Stateless |
| Common use cases | HTTP, HTTPS, FTP, SSH, SMTP | DNS, VoIP, streaming, online gaming |
| Monitoring | Easier to monitor (stateful) | Harder to monitor |
Monitored network ports
While there are 65,535 possible ports, only a subset of those are routinely used and actively monitored. These ports support key services like file transfers, email, web traffic, remote access, and VoIP. Due to their importance, they are common targets for performance issues, outages, or security threats, making them essential for any port monitoring strategy.
Below is a list of commonly monitored ports, including their associated protocols and use cases:
| Port | Protocol/service | Description |
| 20/21 | FTP (File Transport Protocol) | Used for transferring files; port 21 handles commands, port 20 handles data. |
| 22 | SSH (Secure Shell) | Secure remote access to servers and systems. |
| 23 | Telnet | Legacy remote login protocol; monitored for security on older systems. |
| 25 | SMTP | Used to send emails (outgoing mail). |
| 53 | DNS | Resolves domain names to IP addresses. |
| 80 | HTTP | The foundation of unencrypted web browsing. |
| 110 | POP3 | The email retrieval protocol used by mail clients. |
| 123 | NTP (Network Time Protocol) | Synchronizes clocks across systems; essential for time-sensitive operations. |
| 143 | IMAP | Retrieves email with folder and sync support. |
| 161 | SNMP | Monitors and manages network devices. |
| 179 | BGP (Border Gateway Protocol) | Enables routing between large networks (autonomous systems) on the Internet. |
| 443 | HTTPS | Secure web browsing using SSL/TLS encryption. |
| 465 | SMTPS (Secure SMTP) | An older port for sending email securely over SSL (mostly deprecated). |
| 500 | ISAKMP (Internet Security Association and Key Management) | Used for establishing secure IPsec connections. |
| 993 | IMAPS | Secure version of IMAP for encrypted email retrieval. |
| 3306 | MySQL | The default port for MySQL database communication. |
| 3389 | RDP (Remote Desktop Protocol) | Remote access to Windows desktops; commonly targeted in attacks. |
| 5060/5061 | SIP (Session Initiation Protocol) | Manages VoIP calls and multimedia sessions. |
What is port monitoring?
Port monitoring is the process of observing and tracking the status and activity of network ports to ensure that services are running smoothly, securely, and efficiently. It involves continuously checking whether specific TCP or UDP ports on a device or server are open, closed, or experiencing issues, and alerting administrators when something goes wrong.
If a critical port suddenly becomes unreachable, it can indicate a service outage, misconfiguration, or even a cybersecurity threat such as a DDoS attack or unauthorized access attempt.
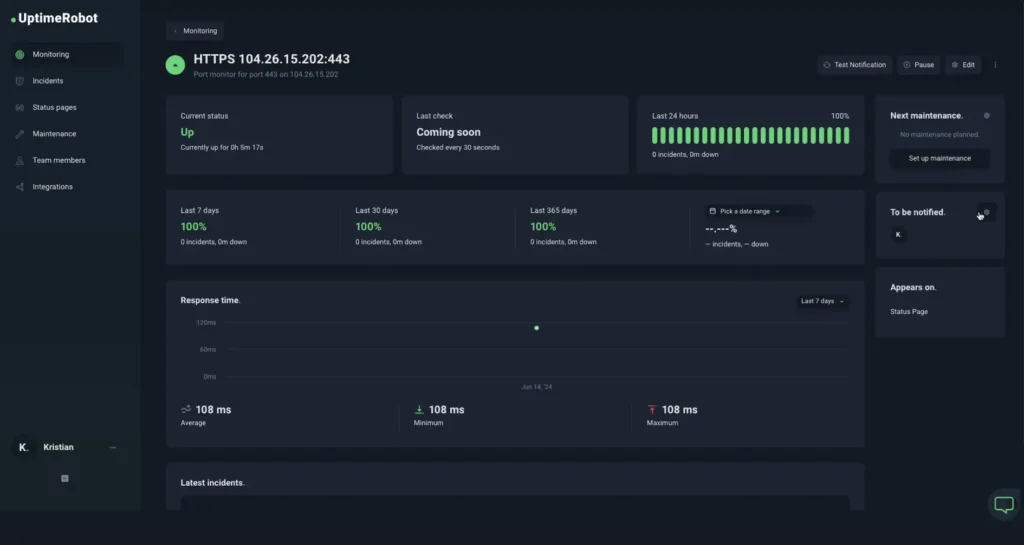
Monitoring tools can provide real-time insights into:
- Port availability (is the service online?)
- Response time and latency
- Unexpected port activity (such as unauthorized open ports)
- Changes in service behavior
- Security risks and anomalies
What port monitoring tells you that uptime alone cannot
Port monitoring answers a more precise question than basic uptime checks. It asks whether a specific service is reachable and accepting connections on the expected port, not just whether the server responds at all.
This matters because many outages are service-level failures. A server can reply to ping and still be unusable. The web server might be down, HTTPS might be blocked, or a database listener might not be running. From a user perspective, the service is broken, even though the host looks “up.”
Port monitoring catches these gaps. By checking ports like 80, 443, 22, 3306, or custom application ports, you validate that the right services are exposed and reachable. If a firewall rule changes, a service crashes, or a process stops listening, port checks fail immediately.
It is especially useful in layered setups. Load balancers, proxies, and firewalls can fail independently of applications. A misconfigured security update can block traffic without touching the app itself. Port monitoring surfaces this class of failure faster than HTTP or application-level checks alone.
Port checks also help confirm deployments and config changes. When services move between ports or protocols, monitoring the expected port verifies that the change actually took effect. This reduces guesswork after deploys.
There are limits to keep in mind. An open port does not guarantee the service behind it works correctly. An application can accept connections and still return errors. That is why port monitoring works best as a middle layer, paired with higher-level checks like HTTP responses or keyword validation.
Alert tuning matters here. Networks are noisy. A single failed connection does not always mean an outage. Reliable port monitoring retries and alerts only after consecutive failures, so teams get signal instead of flapping alerts.
Another advantage is independence. External port monitoring still runs when internal agents or the host itself are unreachable. That outside view often detects issues first during network or firewall incidents.
Port monitoring is most effective when focused. Monitor the ports that define whether users can actually reach your service. When those go dark, availability is already compromised.
How to monitor a port
Monitoring a port means checking if it’s reachable and performing as expected. This helps ensure that the underlying service is running smoothly and securely. Whether you’re tracking performance or watching for signs of a potential attack, the process includes gathering and analyzing a few key metrics.
Key port monitoring metrics
- Uptime: Confirms if a port is reachable and responsive; indicates service availability.
- Response time: Measures how quickly the port replies to a request; helps detect latency issues.
- Bandwidth usage: Tracks the amount of data being sent and received through a port.
- Packet loss: Indicates dropped packets, which can signal congestion or network instability.
- Open/closed status: Detects whether a port is actively listening or unexpectedly closed.
- Connection failures: Counts unsuccessful connection attempts, which could indicate a problem or attack.
- Traffic patterns: Monitors spikes, anomalies, or unusual protocols that could be suspicious.
Curious about the best port monitoring tools on the market? Check out our post on the top 10 port monitoring tools
How to monitor a port (Step-by-step guide)
Using the UptimeRobot port monitoring tool, you can set up monitoring in just a few steps:
- Log in to your monitoring dashboard.
- Create a new monitor.
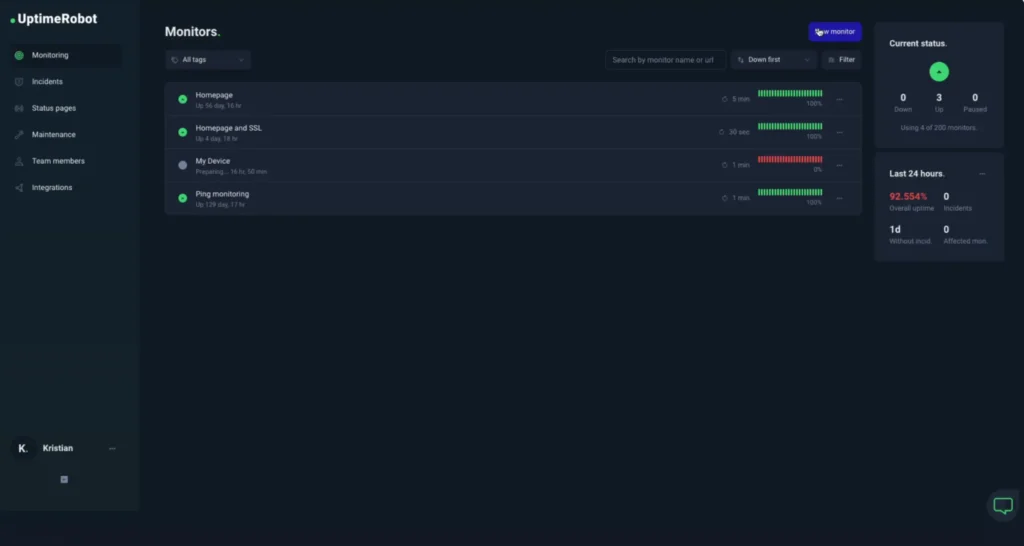
- Go to “Monitoring” > “Port Monitoring.”
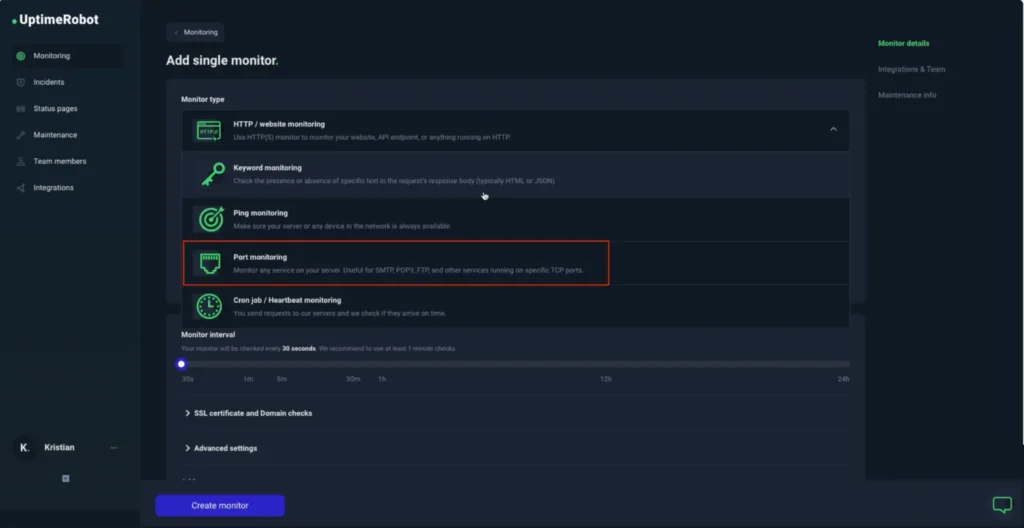
- Enter the IP address or hostname of the device you want to monitor.
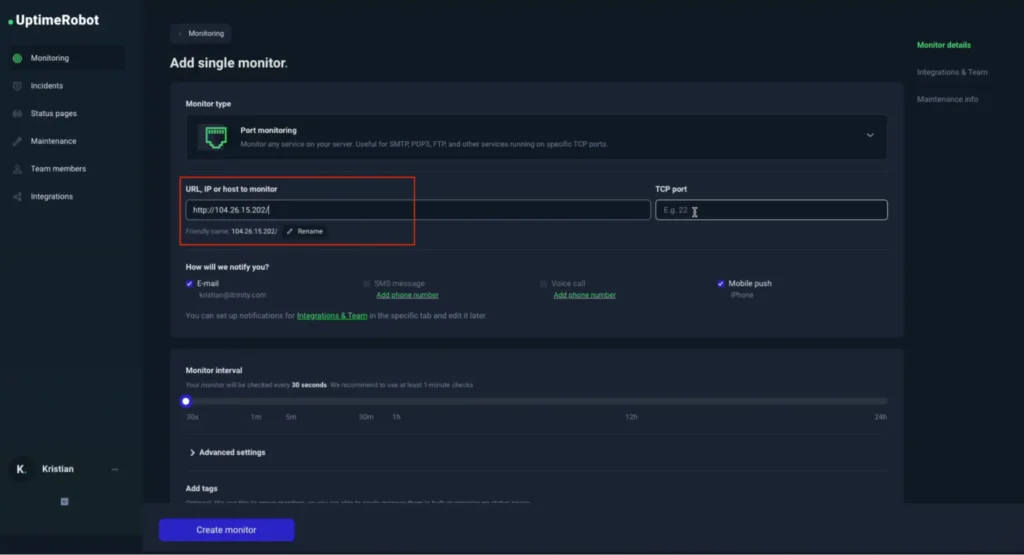
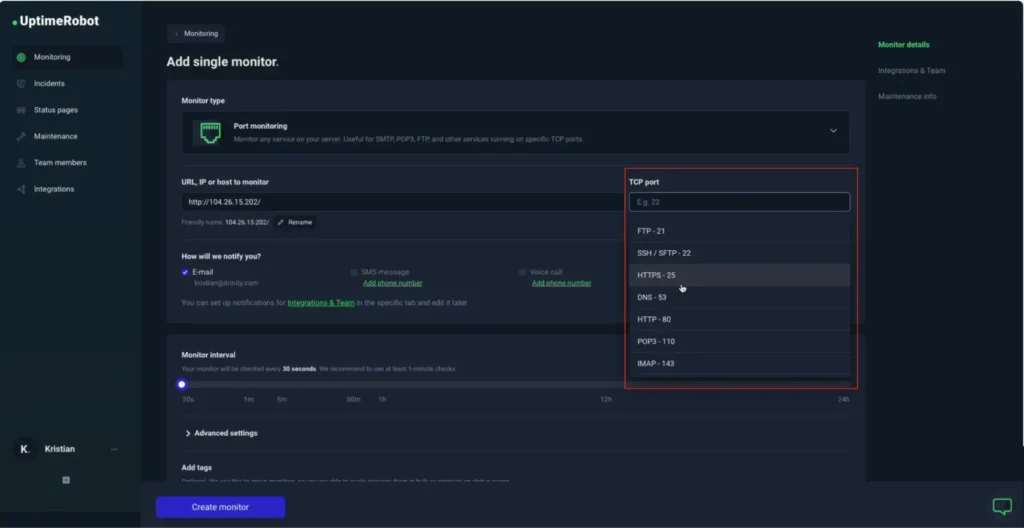
- Choose the port number.
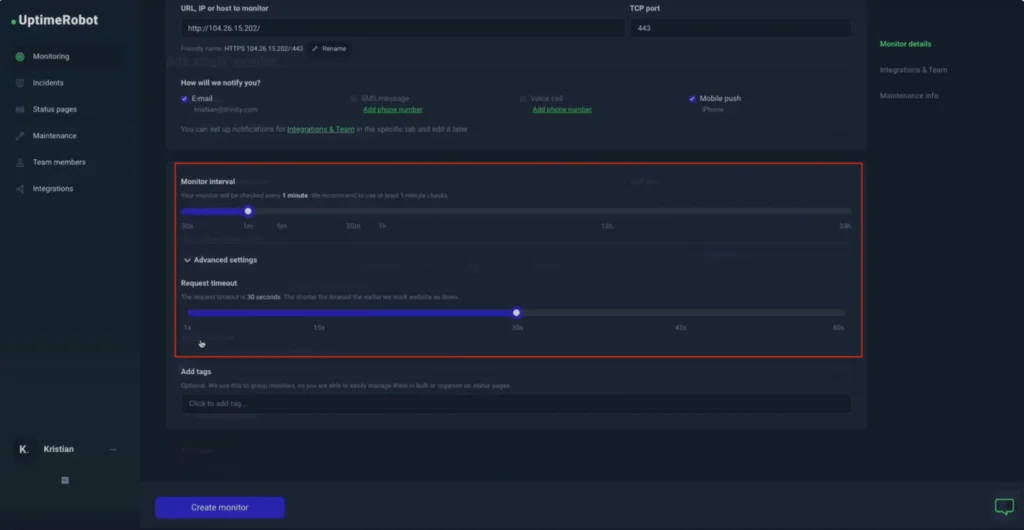
- Set your alert conditions, such as triggering an alert if the port is down for more than 1 minute.
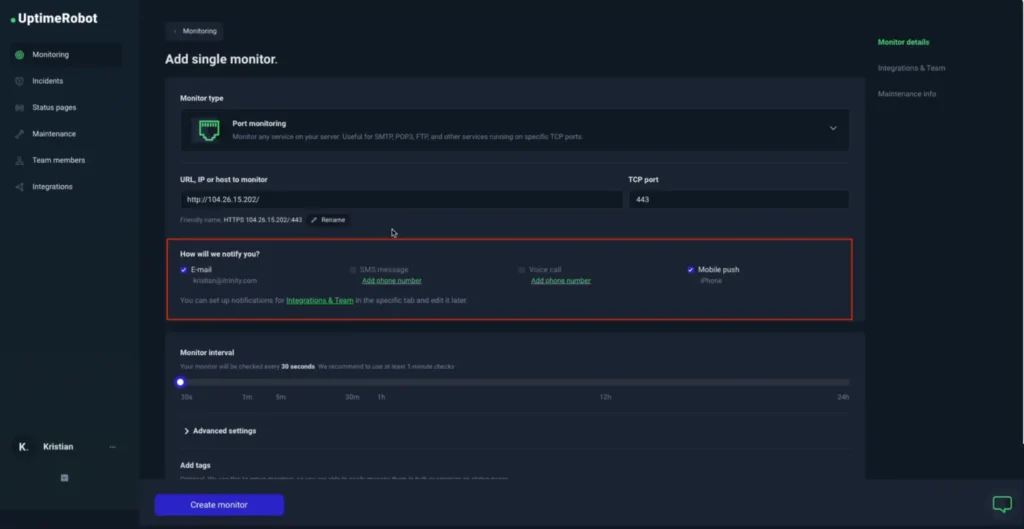
- Choose how you want to be notified (email, SMS, Slack, etc.).
- Click “Create Monitor.
- Start receiving real-time data and alerts based on configured thresholds.
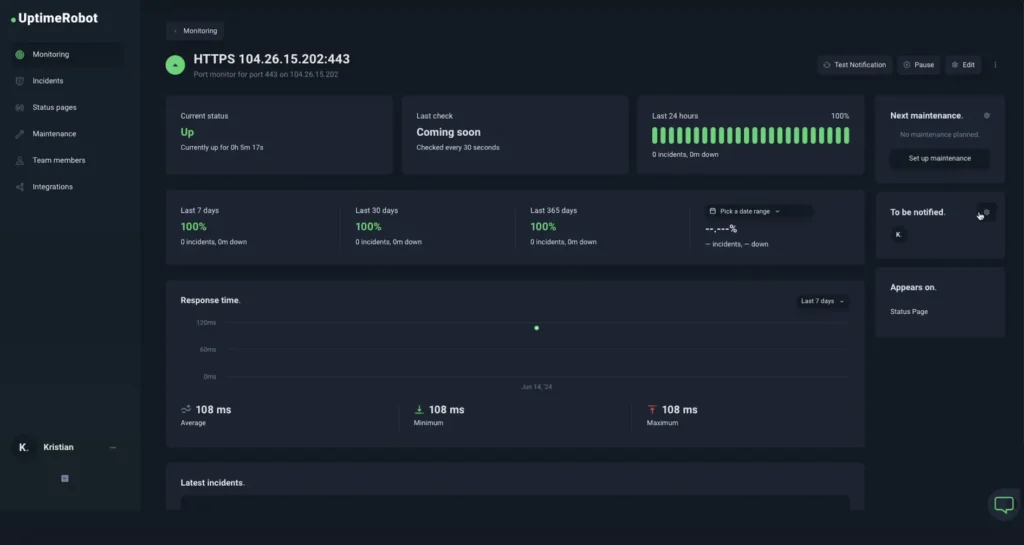
The importance and benefits of port monitoring
Port monitoring keeps an eye on your network and alerts you whenever there’s an issue. For example, if you’re managing a remote team and your company’s VPN service becomes unreachable, employees may lose access to internal tools and resources. This can disrupt productivity until the issue is resolved. Port monitoring helps you catch these problems early so you can act fast.
Here are some key benefits of implementing port monitoring:
- Identify the root cause of network issues
It’s not enough to know a device is overloaded – you need to know why. Monitoring port activity reveals whether constant or heavy traffic is behind a slowdown or service failure.
- Pinpoint faulty or overloaded ports
If a switch is experiencing problems, port monitoring helps determine whether the whole device is affected or just a specific port. This saves time in troubleshooting and avoids guesswork.
- Detect hardware issues like broken cables or patch panels
Intermittent disconnections can be caused by something as simple as a damaged cable. Monitoring helps detect these issues early before they lead to outages.
- Catch configuration and software-level issues
Misconfigurations in speed or duplex settings can silently degrade performance. Port monitoring makes it easier to spot problems like duplex mismatches, protocol drops, or negotiation errors.
- Identify issues like packet loss, flapping, or high error rates
Ports that go up and down (flapping) or show high packet loss can indicate deeper hardware or sync issues. Monitoring gives you the visibility to address these before they escalate.
- Improve network planning and resource management
Knowing which ports and connections are used most helps with capacity planning. It ensures you’re upgrading the right devices and not wasting resources replacing hardware that’s still performing well.
- Spot unauthorized connections
If an unused port suddenly becomes active, it may indicate an unauthorized device on your network. Port monitoring helps detect and alert you to suspicious activity in real time.
Port monitoring has many advantages, with keeping your business online being the most important. It sends alerts as soon as a problem is detected to help prevent downtime.
Monitoring tools like UptimeRobot simplify this process by providing real-time notifications, empowering you to act fast and minimize disruptions. With the right monitoring in place, you can maintain reliable, uninterrupted service and protect your network from costly outages.
FAQ
-
Port monitoring is the process of tracking the status and activity of network ports to ensure services are running properly. It helps detect issues like downtime, misconfigurations, or security threats.
-
Port monitoring helps prevent downtime, identify network performance issues, detect unauthorized access, and ensure critical services remain available and secure.
-
TCP ports use a reliable, connection-based protocol ideal for web and file services. UDP ports are faster but less reliable, commonly used for streaming, gaming, and VoIP.
-
Common ports to monitor include 80 (HTTP), 443 (HTTPS), 22 (SSH), 25 (SMTP), and 53 (DNS). These ports support essential services and are frequent targets for attacks.
-
Monitoring tools track uptime, response times, and failures. If a port becomes unreachable or traffic patterns change unexpectedly, the system alerts you in real time.
-
Yes, many monitoring tools can track both types, though monitoring UDP ports is more complex due to their stateless nature.
-
Tools like UptimeRobot offer easy-to-use dashboards, real-time alerts, and customizable monitoring for both TCP and UDP ports.
-
Absolutely. It helps detect unauthorized connections, port scans, or unusual activity that could signal an attack or breach.
-
Continuous, real-time monitoring is ideal. Most tools allow you to set custom check intervals (e.g. every minute) to ensure constant visibility.
-
No, even small businesses or individuals running web servers can benefit from port monitoring to avoid service interruptions and improve performance.