DNS queries are the foundation of how the internet works behind the scenes. Every time you type a domain name like ‘yourfavewebsite.com’ into your browser, your device (the DNS client) sends out a query to translate that name into the correct IP address, which is something the internet actually understands.
This communication between the client and DNS servers is fast, invisible, and essential for loading websites, apps, and services.
We’ll break down what DNS queries are, how the query process works, the different query types, the role of authoritative DNS servers, and how DNS records keep everything organized. We’ll also touch on common problems and how DNS security features help keep your data safe.
Key takeaways:
- A DNS query is a request from a DNS client to resolve a domain name into an IP address using a structured query message.
- There are three main types of DNS queries: recursive, iterative, and non-recursive, each with its own way of handling the resolution process.
- The DNS resolution process may involve multiple servers, including root servers, TLD servers, and authoritative name servers.
- Common DNS records like A, AAAA, CNAME, MX, TXT, and PTR provide specific instructions for resolving and managing domain data.
- DNS caching improves speed and performance, but incorrect settings or outdated data can lead to resolution failures.
- Security threats like DNS spoofing and cache poisoning are mitigated using tools like DNSSEC and DNS over HTTPS.
What is a DNS query?
A DNS query is a request made by a client computer (usually your device) to a DNS server to find out the IP address tied to a specific domain name. For instance, when you enter UptimeRobot.com, your computer needs the numerical IP address that corresponds to that domain so it can load the site.
This process is part of what’s called the Domain Name System (DNS), which acts like the internet’s phonebook. Instead of memorizing a long string of numbers, users rely on domain names, and DNS takes care of translating them in the background.
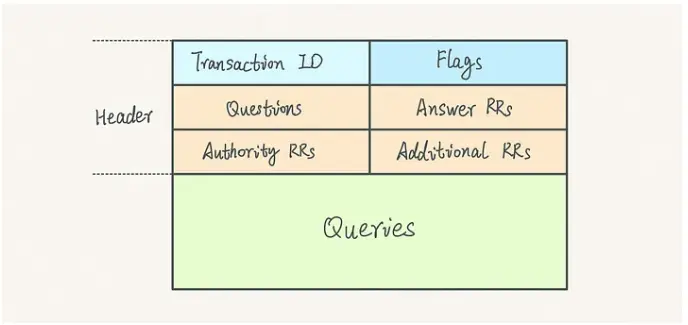
Each DNS query is structured as a query message that typically includes the following parts:
- Header: Contains metadata like the query ID and flags
- Question: Specifies the domain name, query type (like A, MX, TXT), and specified class (usually IN for internet)
- Answer: Returns the resource records if available
- Authority: Lists the authoritative name server(s) for the domain
- Additional: Provides extra information like supporting name server records
When a client sends a query, it may be answered directly if the own cache has the answer, or it might go through a chain of other DNS servers to resolve the name fully.
For most requests, the DNS protocol uses UDP for speed, but TCP may be used when the response is too large for a single packet.
All of this happens in milliseconds, often multiple times per page load, ensuring every image, script, and embedded resource connects to the correct server.
Types of DNS Queries
Not all DNS queries are the same; they vary based on how much work the DNS server is expected to do. There are three main types: recursive, iterative, and non-recursive.
Each plays a special role in the DNS query process and helps you get back the right IP address for the domain you’re trying to reach.
1. Recursive query
A recursive query puts the burden on the DNS server to do all the work. The requesting client asks for an answer, and the server must either:
- return a complete answer (like an IP address), or
- return an error saying the domain name doesn’t exist.
To fulfill this, the server may need to query other DNS servers, climbing the hierarchy from root servers to TLD servers to authoritative DNS servers, until it finds the resource record information.
Recursive queries are common in consumer DNS setups. They make life easier for the client, but they can increase the load on the server.
2. Iterative query
In an iterative query, the DNS server will do its best to help, but it won’t chase the answer for you. Instead, it checks its own data, and if it doesn’t have the answer, it returns a referral answer: the address of another DNS server that might know more.
The client repeats the query process, contacting each new server until the domain name is fully resolved. This keeps each server’s workload lighter but requires the client to do more of the legwork.
3. Non-recursive query
A non-recursive query is the simplest of the bunch. It’s used when the server already has the answer cached (maybe from a previous query), so it can respond instantly. There’s no need to contact additional servers, which speeds things up.
This query type is common between DNS resolvers and authoritative servers, where both parties expect to operate with complete information.
Common DNS records
DNS records are the behind-the-scenes instructions that help the internet run smoothly. Each one plays a specific role in telling servers how to handle requests for a domain. Some are about finding the correct server, others about routing email, and some are just there to offer extra info.
Here are the most commonly used DNS record types and what they do:
- A record (Address record): Connects a domain name to an IPv4 IP address. Without this, a browser wouldn’t know where to send you when you type in something like example.com.
- AAAA record: Like an A record, but for IPv6 addresses instead of IPv4.
- CNAME record (Canonical name record): Points one fully qualified domain name to another. It’s basically an alias. This helps when multiple domains point to the same destination – for instance, www.example.com redirecting to example.com.
- MX record (Mail exchange record): Tells the internet where to deliver email for a domain. Without this, emails might never reach your inbox.
- NS record (Name server record): Shows which DNS servers are authoritative for the domain. It’s essential for delegating DNS responsibilities correctly.
- TXT record (Text record): Originally meant for human-readable notes, but now commonly used to verify domain ownership and set up email security (like SPF, DKIM, and DMARC).
- SOA record (Start of authority): Every DNS zone has one. It holds admin details like who manages the domain and how often records should refresh.
- SRV record (Service record): Used to define services available in a domain, including protocols and port numbers.
- PTR record (Pointer record): Used in reverse DNS lookups to map an IP address back to a domain name. Helpful for email servers and security tools.
Each of these records is part of the DNS namespace tree and contributes to how your DNS query work flows through the system.
How DNS queries work
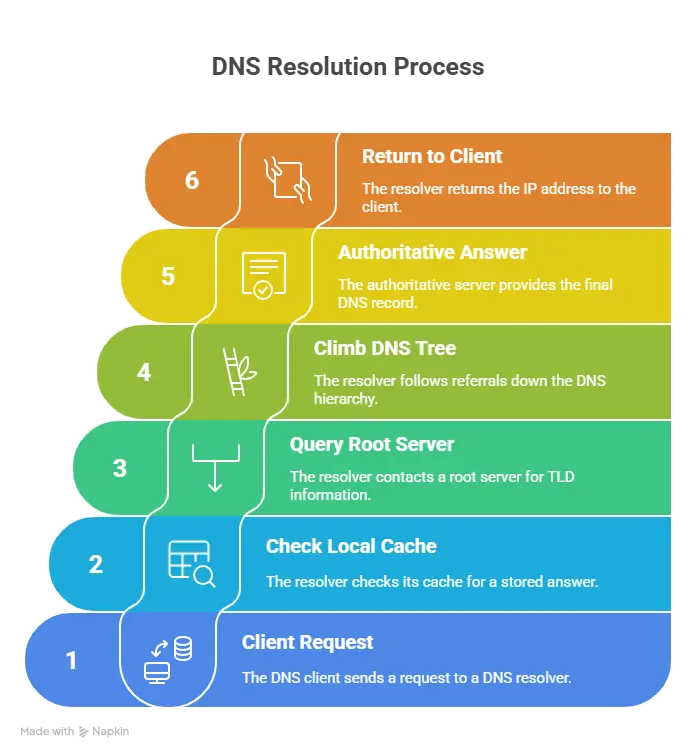
The DNS query process kicks off when a client computer, usually your browser, needs to find the IP address for a domain name. Since your computer doesn’t know it off the top of its head, it sends out a query message to find the answer.
Here’s a breakdown of what happens behind the scenes:
- Client sends a request: Your DNS client (usually built into your operating system) sends a request to a DNS resolver, often provided by your ISP or a public DNS service.
- Check the local cache: If the answer has been stored from a previous query, great! The resolver will pull it from its own cache and return it right away. If not, it starts looking elsewhere.
- Query begins at the top: The resolver contacts one of the root servers. These don’t know the final answer, but they do know which TLD servers (like .com, .net, etc.) to ask next.
- The resolver keeps climbing down the tree: The root server points to the correct TLD server, which then points to the authoritative name server responsible for the exact fully qualified domain name.
- The authoritative server answers: This server holds the actual resource records (like the A record or CNAME) and provides the answer to the resolver.
- The resolver returns the answer to the client: Now the DNS client service has the final IP address and hands it over to your browser which can finally load the site.
This process can involve recursive queries (where the resolver does all the work) or iterative queries (where each server gives the resolver a little nudge in the right direction). If the record is resolved locally, that’s faster. If not, it’ll keep hopping from one DNS server to another until it gets a complete answer.
If something goes wrong, like a bad referral answer or a DNS server timing out, your browser will throw up a “can’t reach this site” error.
How DNS caching helps speed things up
Imagine if every time you wanted to visit a website, your computer had to start the DNS resolution process from scratch: asking the root servers, the TLD servers, and then the authoritative server. That would take forever! So, DNS caching was invented.
When a DNS resolver or client computer gets a response to a query, it saves the result in its local cache.
That way, the next time you visit that same site or request the same IP address, the query operation can be skipped entirely. The resolver just checks its own cache and hands over the answer, no outside help needed.
Caching happens at multiple levels:
- Browser cache: Your web browser stores answers for recently visited sites.
- Operating system cache: Your computer may store DNS info even after the browser is closed.
- Recursive resolver cache: This is often maintained by your ISP or third-party DNS provider (like Google or Cloudflare).
Each resource record comes with a TTL (time to live) value, which determines how long it should be stored in the cache. When the TTL expires, the cached information is discarded, and the client sends a fresh query.
Caching improves performance, but comes with trade-offs. For example:
- If a site changes its IP address but your cached version hasn’t expired yet, you might be directed to the old address.
- A shorter TTL means more frequent updates but more load on the DNS infrastructure.
- A longer TTL reduces server load and speeds up browsing, but at the risk of using outdated info.
This is why high-traffic sites that change often (like news sites) tend to use shorter TTLs, while stable domains stick with longer ones.
Security considerations in DNS queries
DNS was originally designed for speed and scalability, not security. That makes it a bit of a soft target for attackers who want to hijack or manipulate your connection. Understanding the most common threats can help you protect your network and spot when something’s not right.
Here are some of the major risks:
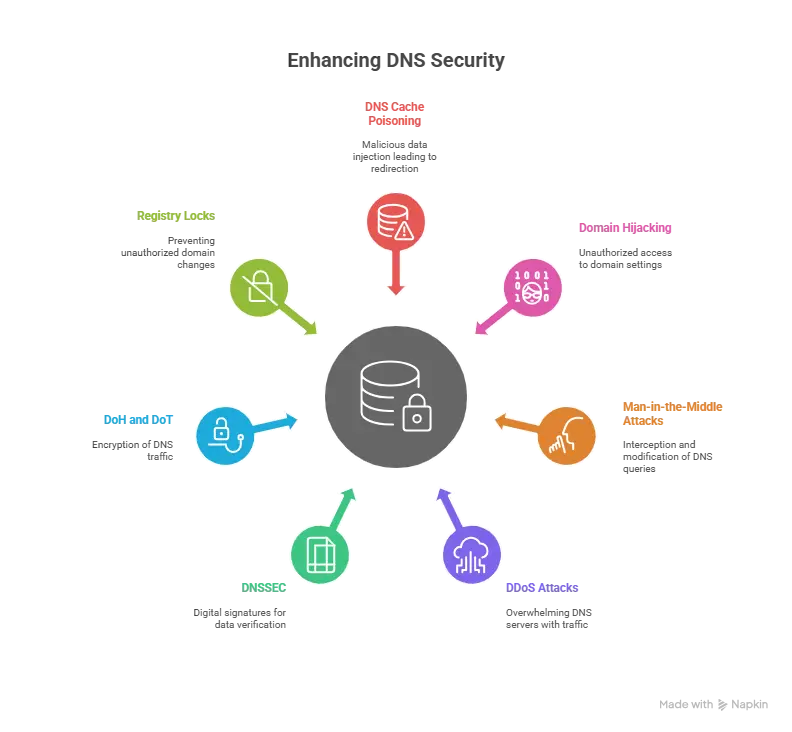
- DNS cache poisoning: This happens when a malicious server slips fake data into the DNS resolver’s cache. The next time the client sends a query for that domain, it gets redirected to a fraudulent IP address.
- Domain hijacking: Attackers gain access to the domain’s settings (often through compromised credentials or social engineering) and change the resource records to point to their own servers.
- Man-in-the-middle attacks: If the communication between the DNS client and the server isn’t encrypted, a third party can intercept and modify the query message on the fly.
- DDoS attacks on DNS servers: By overwhelming authoritative DNS servers or resolvers with traffic, attackers can knock them offline, making websites unavailable.
To help reduce these risks, there are a few modern protections you can (and should) implement:
- DNSSEC (Domain Name System Security Extensions): This adds digital signatures to DNS records so the requesting client can verify the data is authentic and hasn’t been tampered with.
- DNS over HTTPS (DoH) and DNS over TLS (DoT): These encrypt the DNS traffic itself, preventing outsiders from spying on or altering the queries.
- Registry locks: Locking the domain at the registrar level helps prevent unauthorized changes to your fully qualified domain name records.
- DNS filtering: Especially useful for businesses or IoT-heavy (Internet of Things) networks, DNS filtering lets you block access to known malicious domains before a connection is even made.
Bottom line: DNS is essential infrastructure, and leaving it exposed is like leaving the front door of your house wide open. A few extra security layers can make a huge difference.
DNS query failures and troubleshooting
Even with the right setup, DNS queries can sometimes go sideways. When that happens, your browser might throw up an error message like “DNS_PROBE_FINISHED_NXDOMAIN” or just hang forever. Let’s talk about why DNS queries fail and what you can do about it.
Common reasons for failure
Some of the most typical causes include:
- Network issues: Your client computer might not have an internet connection, or something’s blocking the query message from reaching the DNS server. In such cases, using network monitoring or port monitoring tools can help you detect and pinpoint connectivity problems before they affect your DNS or broader site performance.
- Server outages: If the authoritative DNS server or resolver is down, your query won’t go anywhere.
- Bad configurations: A typo in your domain name, expired TTL, or incorrect resource record information (such as misconfigured DNS redirects) can all cause failures.
- DDoS attacks: These can overwhelm single DNS servers, causing timeouts and no responses.
- Cache problems: If the own cache on your system or router contains outdated or poisoned data, your browser might keep trying to resolve to the wrong IP address.
How to troubleshoot
Here are a few steps you can take to diagnose and fix DNS issues:
- Try another device or network: If DNS fails only on one device, the problem is probably local.
- Flush your DNS cache: Clear the local cache to remove stale or corrupted entries. On most systems, this can be done with a simple terminal or command line command.
- Restart your router: It might sound cliché, but power-cycling the router clears out some temporary DNS hiccups.
- Switch DNS servers: If your ISP’s resolver is flaky, try switching to a public DNS server like Google (8.8.8.8), Cloudflare (1.1.1.1), or OpenDNS.
- Check DNS records: Use tools like dig, nslookup, MX lookup or online DNS checkers to see if your domain’s A record, MX record, or PTR record is resolving properly.
- Use UptimeRobot’s DNS monitoring feature: If you manage a website, DNS failures can mean lost traffic and downtime. UptimeRobot’s DNS monitoring tool helps you stay ahead of issues by alerting you when your DNS records change unexpectedly. You can monitor A, AAAA, MX, NS, and other record types for anomalies, so if something breaks, you’ll know before your users do. Learn more here.
If the client repeats the request multiple times and still gets no answer, the DNS client service will usually give up after about 10 seconds. That timeout can feel eternal when you’re just trying to load a webpage, but with the right tools, the root cause is usually fixable.
Enhancing DNS performance
When DNS is fast and reliable, users don’t notice it, it just works. But when it’s slow or broken, the internet feels like it’s falling apart.
Luckily, there are a few smart ways to optimize the DNS query process so your site stays snappy and dependable.
Load balancing and redundancy
To improve performance, many businesses use multiple DNS servers and load balancing. This spreads traffic across several name servers so no single one gets overwhelmed. If one server record goes down, others can still handle requests, keeping everything running smoothly.
Geographically distributed authoritative DNS servers also make a big difference. They help users query the nearest server, which speeds up resolution and cuts down on latency, especially for global sites serving different regions.
Smart caching
A well-tuned local cache can work wonders. The client computer stores previous query results, so if you visit a site again (or even just request a resource on the same domain), the DNS client doesn’t have to ask the authoritative server all over again.
But there’s a catch: the TTL (time to live) setting. If the TTL expires too soon, it leads to frequent repeat queries. If it’s set too high, users might keep seeing outdated info.
For websites that update often, shorter TTLs help keep things fresh. For stable domains, longer TTLs reduce load and improve response times.
Monitoring and tools
If you run a site, keeping an eye on your DNS query work is key. Tools like UptimeRobot, Pingdom, and DNSPerf can alert you to delays, outages, or weird patterns. You’ll be able to spot trouble before your users do and fix it fast.
Did you have a look at our DNS monitoring feature and get intrigued? Sign up now to get DNS monitoring under our Solo, Team, and Enterprise plans. Not ready to make the leap? No worries – you can get 50 monitors for free and upgrade when you’re ready.
DNS in modern networks
DNS might seem like an old-school part of the internet, but it’s more important than ever in today’s hyperconnected world, especially with the explosion of IoT (Internet of Things) devices.
The rise of DNS traffic from smart devices
Every smart fridge, camera, light bulb, and thermostat is a client computer that sends DNS queries.
These devices constantly ask things like: “Where’s the update server?” or “Can I talk to this domain?” Multiply that by millions (or billions), and you’ve got a ton of DNS chatter.
This puts pressure on DNS resolvers and authoritative name servers to respond quickly and accurately, even when requests are coming from devices around the clock. If too many devices hit a single DNS server, it can cause slowdowns or even failures.
Security and performance at scale
In modern networks, it’s not just about speed, it’s also about keeping DNS secure. IoT devices are notoriously bad at cybersecurity, and if their DNS query process is compromised, attackers can redirect traffic, steal data, or flood your servers.
This is where tools like DNS filtering, DNSSEC, and DNS over HTTPS come in. They help protect vulnerable endpoints and ensure that every query operation is going to the correct server and getting a legit response.
As we head into a future filled with even more connected devices, the humble DNS query isn’t going anywhere. If anything, it’s becoming one of the most important moving parts in the modern internet.
Conclusion
DNS queries might work behind the scenes, but they’re a huge part of what keeps the internet running smoothly. Whether you’re typing in a web address, sending an email, or connecting your smart doorbell to Wi-Fi, there’s a DNS query happening in the background, translating a domain name into the IP address your device needs.
Understanding how the DNS query process works can help you troubleshoot issues, improve performance, and build a more secure setup. With more DNS traffic than ever (thanks to IoT and mobile devices), it’s also becoming increasingly important to monitor your DNS activity closely.
If you want to keep tabs on your DNS-related uptime or track failures in real time, consider using a monitoring tool like UptimeRobot. It helps ensure that DNS resolutions are happening when and where they should, giving you peace of mind, better visibility, and fewer surprises.
FAQ's
-
A DNS query is a request sent from a client (like your browser or phone) to a DNS server asking for the IP address of a specific domain name. It’s how the internet turns names like example.com into numbers your device can use to connect.
-
There are three main types:
- Recursive query: The server does all the work and returns a final answer.
- Iterative query: The server returns a referral to another DNS server, and the client follows the trail.
- Non-recursive query: The server gives an answer only if it already knows it, no chasing.
- Recursive query: The server does all the work and returns a final answer.
-
When a DNS query is answered, the result is stored in a local cache for a set time (based on the TTL, or time to live). This helps reduce load on DNS servers and speeds up future requests, unless the TTL expires, in which case a new query is made.
-
Failures can come from network outages, misconfigured settings, expired records, or even DDoS attacks. If the authoritative server can’t be reached or doesn’t respond in time, the client repeats the request or times out entirely.
-
Absolutely. If your name server records aren’t set up right, or if your queries DNS servers take too long to respond, users will experience slower page loads, or no access at all. Tools like UptimeRobot can help detect these issues early.