TL;DR (QUICK ANSWER)
DNS security protects the Domain Name System, the backbone of how the internet works, from being hijacked, spoofed, or taken offline. It ensures users reach the right websites, data isn’t intercepted, and services stay available.
To secure DNS in 2026, organizations should:
- Enable DNSSEC to prevent spoofing and cache poisoning.
- Use encrypted DNS (DoH, DoT, or DoQ) to stop eavesdropping.
- Deploy DNS firewalls to block malicious domains.
- Monitor DNS records for unauthorized changes with tools like UptimeRobot.
- Regularly audit, patch, and restrict access to DNS infrastructure.
Strong DNS security prevents outages, data leaks, and reputation damage, making it a non-negotiable layer of modern cybersecurity.
Every time someone visits a website, sends an email, or connects to an app, DNS quietly makes it happen. It’s the backbone of how the internet routes traffic, and that makes it a prime target.
DNS (Domain Name System) attacks are growing more frequent and more sophisticated, and when they hit, the fallout is immediate: outages, data leaks, broken services, and lost trust.
For teams managing digital infrastructure, DNS security isn’t optional. It’s a critical layer that keeps systems online, users safe, and businesses running.
In this guide, you’ll learn how to assess, strengthen, and future-proof your DNS security.
Key takeaways
- How DNS attacks disrupt services and expose data
- Core technologies that secure DNS traffic
- Best practices for hardening DNS infrastructure
- A maturity model to assess your DNS security posture
- How UptimeRobot supports DNS monitoring and protection
What DNS security is and why it matters
DNS security is about protecting the confidentiality, integrity, and availability of DNS data. It ensures users reach the right destination, attackers can’t tamper with responses, and services stay online.
DNS is what translates easy-to-remember domain names like “example.com” into machine-readable IP addresses. It’s how users find websites, send emails, and connect to apps.
But, DNS was never built with security in mind. The protocol assumes trust, lacks authentication, and sends queries in plaintext. That makes it a prime target for attacks like spoofing, hijacking, and DDoS.
When DNS is compromised, the business impact is immediate:
- Downtime from misdirected traffic or overwhelmed resolvers
- Brand damage if users are routed to phishing or malware
- SEO losses from broken domains or hijacked records
- Data breaches via DNS tunneling or spoofed pages
Simply, securing DNS is business-critical infrastructure protection.
Tip: Learn everything you need to know in our complete guide to DNS monitoring.
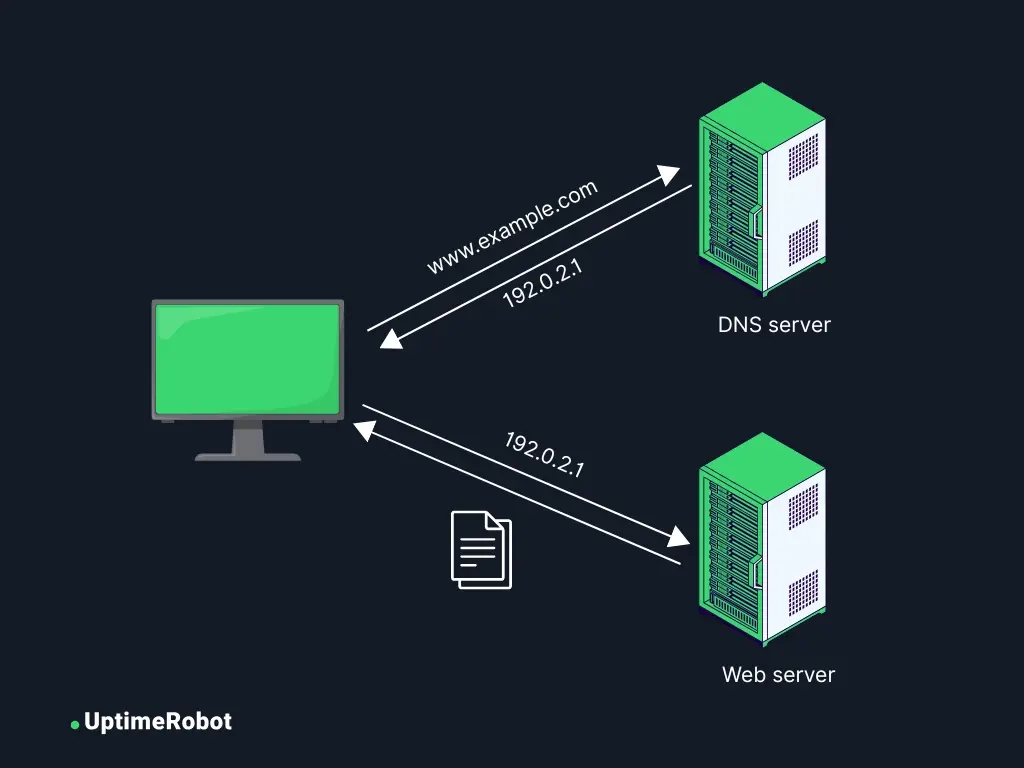
Common DNS attack types
Because DNS translates domain names into IP addresses, compromising it can redirect traffic, exfiltrate data, or take services offline. Understanding how these attacks work is the first step to defending against them.
DNS spoofing and cache poisoning
In this attack, fake DNS responses are injected into a resolver’s cache. Once poisoned, the resolver returns a malicious IP instead of the legitimate one, silently redirecting users to phishing pages or malware.
Older DNS setups are especially vulnerable if they don’t randomize source ports or use predictable transaction IDs.
Mitigation: DNSSEC (covered later), resolver hardening, and response validation.
DNS hijacking
DNS hijacking redirects queries to a rogue resolver, often by altering network or registrar settings. Malware can change a device’s DNS configuration, or attackers might compromise a registrar account to rewrite records.
The result: full control over where traffic goes. Used for credential harvesting, ad injection, or service disruption.
Mitigation: Registrar locks, multi-factor authentication, DNSSEC.
DNS tunneling
Attackers can smuggle data through DNS queries and responses to bypass firewalls. For example, malware might encode data in subdomains like “leakdata.attacker.com”, with the attacker’s server decoding the contents.
Because DNS is rarely blocked or deeply inspected, tunneling often goes unnoticed.
Mitigation: DNS traffic analysis, egress filtering, blocking unnecessary outbound DNS.
DDoS amplification attacks
DNS can be abused in large-scale DDoS attacks by sending small queries with a spoofed IP (the victim’s). Open resolvers reply with oversized responses, flooding the target with amplified traffic.
This was one of the techniques used in the 2016 Dyn outage that disrupted services like Twitter and Netflix.
Mitigation: Block open resolvers, limit response size, rate-limit queries.
NXDOMAIN and random subdomain attacks
NXDOMAIN attacks flood resolvers with queries for non-existent domains, exhausting CPU and memory. A variation (random subdomain attacks) bombards authoritative servers with thousands of unique subdomains, bypassing caches and overwhelming DNS infrastructure.
Mitigation: Rate-limiting, query throttling, anomaly detection.
Each of these attack types targets different parts of the DNS stack, from local resolvers to authoritative servers. Knowing how they work helps teams build more resilient systems and choose monitoring tools that can detect anomalies early.
Key DNS security technologies
To reduce risks, several DNS security technologies have emerged. Each tackles a different part of the problem: authenticity, privacy, or filtering.
Let’s break down the core ones you should know.
DNSSEC (Domain Name System Security Extensions)
DNSSEC protects the authenticity of DNS responses. It uses cryptographic signatures to prove that the DNS data came from the correct source and hasn’t been tampered with.
How it works:
Each DNS zone signs its records with a private key. Resolvers verify the response using the corresponding public key and follow a chain of trust up to the root zone. If the signature is invalid or missing, the query fails instead of returning false data.
Limitations:
DNSSEC doesn’t encrypt DNS traffic, it only verifies integrity. It can also be tricky to configure and maintain, especially for teams unfamiliar with key rollover and DS record delegation.
Still, enabling DNSSEC blocks entire categories of spoofing and cache poisoning attacks.
Encrypted DNS protocols (DoH, DoT, DoQ)
Plaintext DNS queries expose browsing habits to anyone on the network. Encrypted DNS protocols solve this by wrapping DNS traffic in encryption, blocking eavesdropping and tampering.
Here’s how they compare:
| Protocol | Encryption Layer | Port | Use Case | Pros | Cons |
| DoH (DNS over HTTPS) | HTTPS (TLS) | 443 | Browsers, mobile apps | Blends with web traffic, hard to block | Bypasses system DNS, harder to control in enterprise |
| DoT (DNS over TLS) | TLS | 853 | System-level DNS | Easier to monitor in managed networks | Easier to block or fingerprint |
| DoQ (DNS over QUIC) | QUIC (UDP-based TLS) | varies | Edge networks, mobile | Low latency, resilient to packet loss | Still experimental, limited support |
Popular encrypted resolvers:
- Cloudflare 1.1.1.1
- Google 8.8.8.8
- Quad9 9.9.9.9
Teams can configure clients to use public encrypted resolvers or deploy internal DoH/DoT endpoints with policy controls.
DNS firewall and protective DNS
DNS firewalls block queries to known malicious domains like phishing sites, botnets, or C2 servers before connections are made. Protective DNS takes this further by using real-time threat intelligence and behavioral analysis to flag suspicious activity.
These solutions help:
- Prevent malware callbacks and phishing clicks
- Enforce acceptable use policies
- Monitor DNS traffic for anomalies
Common tools:
- Cisco Umbrella
- Quad9
- Cloudflare Gateway
They’re well-suited to enterprises, ISPs, and SMBs that want centralized DNS control without installing agents on every device. You can deploy them at the resolver level, on endpoints, or as a network-level policy.
Each of these technologies addresses a different risk: DNSSEC protects against spoofing, encrypted DNS hides queries from prying eyes, and DNS firewalls block known threats.
Used together, they form a layered defense that makes DNS harder to exploit.
DNS security best practices
Here’s how to approach DNS security with practical, enforceable steps.
Use a reputable DNS provider with built-in DDoS protection
Choose providers that offer anycast routing, traffic filtering, and automated failover to withstand large-scale attacks.
Look for:
- Built-in DDoS mitigation
- Global DNS networks
- Real-time query monitoring
Examples: Cloudflare, AWS Route 53, NS1
Enable DNSSEC for authenticity
DNSSEC adds cryptographic signatures to your DNS records, making it harder for attackers to spoof responses or poison caches.
How to implement:
- Enable DNSSEC via your registrar or provider
- Publish DS records at the parent zone
- Test with tools like dnssec-analyzer.verisignlabs.com
Implement encrypted DNS wherever possible
Use DoH, DoT, or DoQ to prevent DNS traffic from being intercepted or altered in transit.
In practice:
- Set public resolvers on endpoints (e.g., 1.1.1.1, 8.8.8.8)
- Deploy internal DoH/DoT for managed devices
- Block plaintext DNS traffic where appropriate
Restrict zone transfers and use access controls
Zone transfers (AXFR) can expose your entire DNS map if left open.
Do this:
- Disable AXFR unless needed
- Limit transfers to known IPs
- Use TSIG for authenticated transfers
Also, apply role-based access and MFA to DNS admin accounts.
Monitor for anomalies
DNS traffic reveals early warning signs of compromise, especially with tunneling or hijacks.
Monitor for:
- Spikes in query volume
- Requests for strange or random subdomains
- High-entropy or algorithmically generated domain names
Tools: Zeek, Security Onion, DNS firewall logs, SIEM integrations
Maintain redundant DNS servers
Avoid single points of failure. Use multiple nameservers on different networks or providers so your domain stays reachable during outages.
Checklist:
- Use geographically distributed nameservers
- Test failover regularly
- Don’t rely solely on your registrar’s DNS
Keep DNS software patched and automate updates
Unpatched DNS software can expose you to known exploits.
Tips:
- Use a configuration management tool (like Ansible) to automate updates
- Subscribe to security bulletins from your provider or software vendor
- Periodically audit DNS logs and configs for drift
Train teams on DNS-related threats
Most domain hijacks and phishing campaigns begin with human error.
Focus training on:
- Phishing awareness
- Safe registrar practices
- Spotting DNS red flags in domain lookups and URLs
DNS security requires continuous monitoring, strict access controls, and regular audits. As your infrastructure evolves, revisit these practices to keep your DNS layer resilient.
DNS security maturity model
A DNS security maturity model helps teams assess where they stand and identify what to improve next.
This model has three levels: foundational, proactive, and advanced/integrated. Each builds on the last, moving from basic hygiene to full integration with your broader security and observability stack.
Level 1 – Foundational
At this stage, DNS security is minimal or reactive. Teams may rely on default registrar settings, lack visibility into DNS changes, and often don’t monitor for suspicious activity.
Key characteristics:
- No DNS change tracking: Zone file changes go unlogged or are only tracked manually.
- No alerting on DNS anomalies: If a record is modified or removed, no one knows until something breaks.
- Infrequent DNS audits: Records may be stale, misconfigured, or expose internal services.
- Lack of DNSSEC: DNSSEC aren’t enabled, leaving DNS responses vulnerable to tampering.
Example: A marketing team launches a campaign using a subdomain, but forgets to remove it. Months later, an attacker hijacks the unused subdomain to serve phishing pages. No alerts were triggered because DNS changes weren’t monitored.
Level 2 – Proactive
Teams at this level start treating DNS as part of their security perimeter. They implement monitoring, alerting, and basic controls to detect and respond to threats faster.
Key improvements:
- DNS monitoring tools in place: Services like UptimeRobot track DNS record changes and alert teams in real time.
- DNSSEC enabled: Responses are cryptographically signed to prevent spoofing.
- Regular audits scheduled: DNS records are reviewed quarterly or monthly to remove unused entries and check for exposure.
- Access control enforced: Only specific roles can modify DNS records, often with two-factor authentication or role-based access.
Example: A DevOps team uses UptimeRobot to monitor A and CNAME records for production domains. When a misconfigured record is accidentally pushed during a CI/CD deployment, the team gets an alert and reverts it within minutes, avoiding downtime.
Level 3 – Advanced / integrated
At this stage, DNS security is fully embedded into the organization’s security and observability workflows. DNS data is treated as a telemetry source and integrated into SIEM (Security Information and Event Management) or SOAR (Security Orchestration, Automation, and Response) systems.
Key characteristics:
- DNS logs integrated with incident response: Suspicious queries or record changes trigger automated playbooks.
- Threat intelligence feeds used: DNS queries are cross-referenced with known malicious domains.
- DNS monitoring tied to uptime and performance: Teams correlate DNS issues with service degradation or outages.
- Automated rollback of changes: DNS misconfigurations can be reverted automatically based on predefined rules or anomaly detection.
Example: A platform team integrates DNS logs with Splunk On-Call. When a TXT record is modified outside of a maintenance window, the system flags it, rolls back the change, and notifies the security team. The incident is logged and linked to a JIRA ticket for follow-up.
Understanding your DNS security maturity helps prioritize investments and avoid blind spots. Whether you’re just starting to monitor DNS changes or already integrating logs into your SIEM, knowing your level gives you a clear path forward.
How to audit your DNS security
DNS misconfigurations are often invisible until something breaks or gets exploited. A simple, regular audit can uncover weak spots and help teams stay proactive.
Use the checklist below to assess your current DNS security posture. You can fill this out quarterly, during infrastructure changes, or after onboarding new domains.
| Control | Description | Verified (Yes/No) |
| DNSSEC enabled | Digital signatures validate DNS responses | |
| Encrypted DNS used | DoH/DoT implemented to prevent plaintext queries | |
| Registrar lock active | Prevents unauthorized changes to domain ownership | |
| DNS logs monitored | Integrated with SIEM or DNS-specific monitoring | |
| Backup resolvers configured | Secondary providers set for redundancy | |
| Zone transfers restricted | AXFR disabled or limited to trusted IPs | |
| DNS change alerts enabled | Notifications triggered on DNS record modifications | |
| Role-based access enforced | RBAC and MFA applied to DNS management platforms | |
| Expired/stale records removed | Unused records regularly audited and deleted |
Tip: Treat DNS like any other critical system: log changes, review access, and test failover. This simple checklist can prevent costly outages or security incidents down the line.
How UptimeRobot helps strengthen DNS security
DNS issues often go undetected until users are affected. UptimeRobot provides real-time monitoring and alerts that help teams identify problems early and maintain system integrity.
Detect DNS resolution failures instantly: Receive alerts when DNS records stop resolving, point to the wrong IP, or are removed unexpectedly.
Monitor multiple DNS servers: Check resolution across different nameservers or providers to catch inconsistencies and propagation issues.
Get alerts before users notice: Configure notifications via email, SMS, Slack, voice call, API, or webhook. Respond quickly before problems escalate.
Complement DNSSEC and encrypted DNS: UptimeRobot helps detect failures even in secured setups. Use it to catch misconfigurations in DNSSEC, DoH, or DoT endpoints.
Monitor from multiple global location: Test resolution from over 20 monitoring locations to detect regional or provider-specific DNS outages.
UptimeRobot adds an essential layer of observability to DNS. It helps you act quickly, reduce downtime, and stay ahead of potential threats.
Future of DNS security
DNS security is evolving to keep pace with new threats, network models, and encryption standards. Here are the key developments to watch.
DNS over QUIC (DoQ) will gain adoption
DoQ combines DNS encryption with better performance over unreliable or high-latency networks. It reduces handshake time and is resilient to packet loss, making it ideal for mobile, edge, and satellite environments.
As more resolvers and clients add support, DoQ is expected to complement or even replace DoH and DoT in some cases.
AI and machine learning in DNS telemetry
Traditional rule-based detection cannot keep up with evasive DNS threats like fast-flux domains or domain generation algorithms (DGAs).
Security platforms are increasingly using AI and machine learning to analyze DNS query patterns and detect anomalies in real time. Feeding DNS logs into SIEMs and behavior-based detection tools is becoming essential.
Post-quantum cryptography and DNSSEC
Quantum computing poses a future risk to DNSSEC, which relies on algorithms like RSA and ECDSA. Researchers are developing post-quantum DNSSEC algorithms to resist quantum attacks.
While quantum-safe DNSSEC is not yet in production, key size expansion and algorithm agility will shape future deployments.
DNS security at the edge and in IoT networks
Edge computing and IoT devices often rely on lightweight, insecure DNS stacks with minimal oversight. As these devices proliferate, DNS becomes a critical control point for both connectivity and security.
Expect to see more localized DNS monitoring, encrypted queries, and DNS firewalls built into edge gateways and IoT platforms.
The future of DNS security is active, not reactive. As protocols evolve and threats adapt, teams need to rethink how they manage and monitor DNS. From encryption to AI-driven detection, the tools are here, but they only help if you use them.
Conclusion
DNS is often overlooked until it breaks. When it does, it can take your entire system down with it. From hijacked records to silent outages, DNS failures are a serious risk to uptime, security, and trust.
Securing DNS isn’t just a technical task. It’s an ongoing process that combines the right controls, regular audits, and reliable monitoring. Strong DNS hygiene makes your infrastructure more resilient and your team faster to respond when something changes.
Start protecting your DNS layer with UptimeRobot: Monitor DNS resolution, detect misconfigurations, and receive instant alerts before users are impacted.
FAQ's
-
DNSSEC verifies the authenticity of DNS responses using cryptographic signatures. Encrypted DNS (like DoH or DoT) protects the privacy of DNS queries by hiding them from third parties. DNSSEC ensures data integrity; encrypted DNS protects data in transit. They are complementary.
-
Common signs include unexpected redirects, invalid SSL certificate warnings, or users being sent to phishing pages. Monitoring tools like UptimeRobot can alert you to DNS record changes or failed resolutions.
-
It can, but only slightly. Technologies like DNSSEC and encrypted DNS may add milliseconds to lookup times, but the trade-off for added security is often worth it. Most users won’t notice the difference. -
Ideally, review logs weekly or after any DNS change. Look for unusual queries, spikes in traffic, or changes to records. Integrating DNS logs into a SIEM can help automate alerting and detection.
-
DNS monitoring is included in UptimeRobot’s Solo, Team, and Enterprise plans. Free and Legacy users still have access to core monitoring features, but advanced DNS monitoring is available with paid plans for improved security and uptime tracking.