TL;DR (QUICK ANSWER)
What Is a DNS Attack and How to Protect Your Website from It?
A DNS attack targets the Domain Name System to redirect traffic, take websites offline, or steal data. Common methods include DDoS, cache poisoning, hijacking, and tunneling. Protect your site by using a reputable DNS provider, enabling DNSSEC, enforcing strong access controls, monitoring DNS records, and setting up automated DNS alerts. Regular auditing and redundancy help ensure uptime and security.
You can secure your servers and lock down your network, but if your DNS (Domain Name System) is exposed, attackers can still take your services offline. DNS sits in front of every request that reaches your infrastructure. When it’s tampered with, things break long before your application logs show anything unusual.
Recent incidents have shown how fragile this layer can be. In late 2024, several platforms experienced sudden outages caused by DNS hijacks and poisoned caches.
Nothing was wrong with their servers. The problem started at the DNS level and took time to diagnose because the symptoms looked like unrelated network or application failures.
DNS attacks work because the system was designed for speed and global trust. When something goes wrong, users feel the impact immediately.
The advantage for defenders is that DNS issues leave patterns. With the right monitoring in place, you can see the earliest signs and act before users notice.
Key takeaways
- DNS attacks can disrupt your services even when your servers are healthy
- Attackers target dns because it is trusted, distributed and fast
- Early detection relies on watching for unusual error rates, TTL changes, resolver inconsistencies and unexpected record updates
- Strong DNS configuration, secure registrar access and redundancy reduce your exposure
- Continuous DNS monitoring helps catch issues early and shorten incident response times
Understanding how DNS works
DNS is the system that turns domain names into IP addresses. Every time someone visits your site, their device asks DNS which server it should connect to.
This lookup happens fast, but several layers are involved, and each one can be targeted or manipulated.
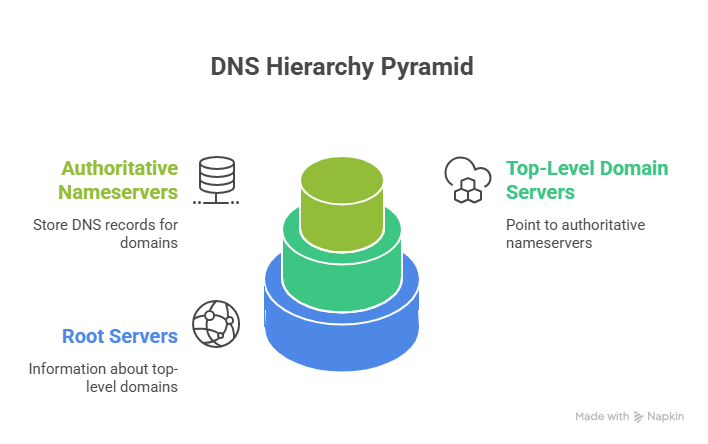
The DNS hierarchy
The lookup path follows a predictable structure:
- Root servers hold information about top level domains
- Top level domain servers point resolvers to the correct authoritative nameservers
- Authoritative nameservers store the actual DNS records for your domain
A resolver moves through these layers until it finds the answer. Most of the time, the process is cached, but when a resolver needs fresh information, it must query upstream servers. These steps are where attackers look for weak spots.
Recursive resolvers
Most users rely on recursive resolvers from their ISP or a public service like Google or Cloudflare. The resolver handles the full lookup on the user’s behalf and caches the result.
If an attacker poisons the resolver’s cache or tricks it into storing a forged record, every user behind that resolver will see the wrong destination.
Where DNS is vulnerable
DNS was not designed with strong authentication. That leaves several places where attacks can happen:
- Caches that accept forged responses
- Open resolvers that answer queries from anywhere
- Registrar accounts that can be compromised
- Authoritative servers with weak access controls
- Misconfigured zone files or record updates
Even small weaknesses can cause global issues because DNS responses are trusted and widely cached.
What is a DNS attack?
A DNS attack is any attempt to tamper with the systems that translate domain names into IP addresses. If an attacker can influence this process, they can redirect users, disrupt availability or make your site appear offline even when your servers are healthy.
Most DNS attacks fall into two categories. The first targets resolvers or caches, hoping to feed them forged answers that users will trust.
The second targets authoritative nameservers or registrars, which lets attackers rewrite records at the source. Both approaches create the same effect. Users reach the wrong destination, or they cannot reach your domain at all.
DNS is a frequent target because it is distributed and trusted by design. Resolvers accept responses quickly, nameservers are updated constantly, and registrars often control hundreds or thousands of domains at once. When any part of this chain is compromised, the impact spreads fast.
A DNS issue is not always an attack. Misconfigurations, expired records and propagation delays can look similar.
The difference is intent. Attacks leave patterns such as sudden record changes, inconsistent resolver answers, unusual TTL values or query behavior that does not match normal traffic. These clues help you separate accidents from deliberate manipulation.
Main types of DNS attacks
DNS attacks usually aim to overload DNS infrastructure or manipulate how queries resolve. Below are the most common types, explained briefly with key signals and practical defenses.
DNS amplification and DDoS
Amplification attacks use open DNS resolvers to generate large response packets that are sent to a spoofed target. Even a small query can produce a large response, which quickly overwhelms networks and makes DNS queries fail.
| What it looks like | What helps |
| Slow DNS responses across multiple regions | Limit open resolvers |
| Rising timeout rates | Restrict ANY queries |
| Traffic from sources your service does not normally receive | Use rate limiting on authoritative servers |
These attacks are loud once you know what normal traffic looks like.
DNS cache poisoning
Cache poisoning inserts forged DNS data into a resolver’s cache. Once the resolver stores the fake record, every user behind it is silently redirected to the wrong server.
| Common indicators | What helps |
| Resolver answers that do not match authoritative records | Enable DNSSEC validation |
| TTL values that feel unusually short or long | Keep resolvers patched and hardened |
| IP changes with no internal deployment | Monitor for unexpected DNS shifts |
Poisoning usually reveals itself through subtle inconsistencies between resolvers.
DNS hijacking
Hijacking changes DNS records at the source. Attackers often compromise registrar accounts or DNS control panels, then update records to point users to attacker controlled servers.
| Warning signs | What helps |
| A or CNAME records pointing to unfamiliar IPs | Use registrar lock |
| Name servers changed without approval | Require two factor authentication |
| TTL drops that were not part of a planned update | Monitor every authoritative change |
Hijacking has the widest blast radius because it affects the domain at its source.
DNS tunneling
Tunneling hides other traffic inside DNS queries or responses. Attackers often use it to exfiltrate data or maintain command and control channels in restricted environments.
| Patterns to watch | What helps |
| Very long or unusual subdomains | Monitor query entropy and lengths |
| Large TXT responses from unknown domains | Block suspicious outbound DNS where possible |
| Repeated queries to the same external domain | Compare traffic to baseline patterns |
Tunneling typically blends into normal DNS chatter unless you inspect patterns closely.
Emerging threats
DNS abuse continues to evolve with new techniques that hide inside encrypted protocols or exploit trust between DNS providers.
| Trends worth tracking | What helps |
| DNS over HTTPS masking suspicious activity | Use endpoint level DNS visibility |
| Domain shadowing on compromised accounts | Audit registrar access regularly |
| Machine generated subdomains linked to malware | Use anomaly detection on resolver logs |
| Supply chain compromises at DNS providers | Use multiple DNS providers and verify zone integrity |
These threats rely on defenders not monitoring DNS deeply enough.
How to detect a DNS attack early
DNS attacks rarely start with a full outage. They usually show up as small deviations in how your domain resolves. If you know what to watch for, you can catch the attack quickly.
Look for unusual resolution patterns
The first signs of a DNS attack often appear in error counts and lookup behavior. These patterns stand out:
- A sudden spike in NXDOMAIN responses
- SERVFAIL errors appearing in clusters
- TTL values dropping unexpectedly
- Query floods hitting your resolvers from a single IP or region
These shifts usually happen before traffic loss or visible downtime.
Review DNS logs and query analytics
Your resolver and authoritative server logs offer a clear view of what is happening behind the scenes. Look for:
- A large increase in TXT or ANY queries
- Repeated requests for non existent subdomains
- Surges in requests that bypass your normal traffic pattern
- High entropy domain queries, which often indicate tunneling or command and control traffic
Even basic DNS analytics tools can surface these patterns quickly.
Use multi location monitoring to confirm the scope
DNS attacks often affect one region before spreading. Multi location monitoring helps you confirm whether the issue is isolated or global.
For example:
- If only one region fails to resolve your domain, a local resolver or ISP may be compromised.
- If multiple regions return different IPs for the same domain, that points to poisoning or hijacking.
- If all regions time out at the same time, your authoritative servers may be overloaded or under attack.
Context like this helps teams respond accurately instead of chasing the wrong problem.
How to prevent and mitigate DNS attacks
DNS security depends on reducing your attack surface, protecting your registrar and name servers, and catching issues before they spread. A few targeted controls make it much harder for attackers to tamper with your DNS layer.
Strengthen your DNS configuration
Hardening your DNS setup removes the easiest entry points attackers rely on. These steps build a stronger baseline:
- Disable zone transfers unless required.
If you must allow them, restrict access to approved IPs and protect transfers with TSIG. An open zone transfer exposes your entire DNS structure. - Enable DNSSEC to prevent forged responses.
DNSSEC signs your DNS records so resolvers can verify authenticity. This helps stop cache poisoning and spoofing attacks. - Review and minimize wildcard records.
Wildcards make it easier for attackers to create or abuse subdomains. Only use them when you have a clear operational need. - Audit your TTL values.
Long TTLs preserve poisoned data, while extremely short values increase load on resolvers. Adjust TTLs to balance safety and performance. - Check for outdated or unused records.
Stale entries create unnecessary exposure. Clean them up to reduce your attack surface.
Secure your registrar and name servers
Your registrar account controls your entire domain. If someone gains access, they can redirect traffic anywhere. Protect it with two factor authentication and limit access to a small, trusted group.
Enable domain lock or registrar lock so no one can change name servers or transfer your domain without authorization. If your registrar supports registry lock, use it. It adds an extra layer of manual verification for any change.
Distribute your authoritative name servers across different regions and networks. If they all sit in the same cloud environment, a single outage or attack can bring everything down.
Deploy redundancy and failover systems
Use more than one DNS provider. If your primary provider is targeted by a DDoS attack or experiences an internal failure, your secondary provider continues serving records without interruption.
If supported, use anycast DNS. Anycast distributes queries across multiple global locations, reduces latency, and helps absorb spikes in malicious traffic.
Combine this with health checks and automated failover to keep your domain available during regional incidents.
Use continuous monitoring and alerting
DNS attacks are easier to stop when you detect them early. Continuous monitoring helps you identify unusual response times, record changes, or resolver failures.
Watch for:
- Record changes you did not deploy
- TTL values dropping unexpectedly
- Resolution failures that appear in one region before another
Monitoring tools like UptimeRobot can check DNS resolution from multiple locations, alert you when records change, and flag failures before customers report them.
Send alerts through the channels your team already uses. Slack, PagerDuty, and email integrations help your team move on the issue right away.
Real-world DNS attack examples and lessons learned
DNS attacks have taken down major platforms, exposed sensitive information and caused major financial and operational damage. Real incidents make the risks much easier to understand.
They show how these attacks actually unfold, which weak points get exploited and what could have prevented the worst outcomes. Here are a few examples and the lessons teams learned from them.
Case study 1: Dyn DDoS attack (October 2016)
On October 21st, 2016, Dyn, a major DNS provider, was hit by a massive DDoS attack that disrupted DNS for large parts of North America and Europe.
At the peak, tens of millions of IPs from a botnet flooded Dyn’s infrastructure, causing DNS queries to timeout or fail entirely. Services including Twitter, Spotify and Netflix were rendered inaccessible or unreliable.
What failed: Dyn’s single-provider setup became a critical choke point, and the attack leveraged many IoT devices infected with the Mirai botnet.
Lessons: Use multiple DNS providers to avoid single points of failure; monitor DNS resolver availability; treat your DNS provider as part of your threat surface.
Case study 2: Sea Turtle DNS hijacking campaign (2017-2019)
The Sea Turtle campaign was a state-aligned DNS hijacking operation targeting telecommunications and government agencies across the Middle East, North Africa, and beyond.
Attackers compromised registrars and manipulated DNS records, redirecting traffic and harvesting credentials through changed authoritative name servers.
What failed: Registrars and DNS providers were treated as trusted infrastructure rather than threat vectors; record changes went unnoticed.
Lessons: Close registrar access, track every record change, and apply monitoring that detects name-server or registrar drift.
Case study 3: Misconfiguration incident – Google DNS outage (March 2020)
In March 2020, Google Public DNS experienced an outage that affected millions of users, not from a direct attack, but from a configuration error. While less glamorous than a deliberate attack, this incident demonstrates how DNS misconfigurations mimic attack behavior.
What failed: Internal change propagated incorrectly; monitoring and rollback mechanisms failed to catch the issue before users experienced latency or failed lookups.
Lessons: Treat internal DNS changes with the same rigour as external threats, and implement validation, staging and rollback for DNS updates.
How UptimeRobot helps protect against DNS attacks
UptimeRobot gives you early visibility into DNS problems by tracking how your domain resolves and alerting you when something changes unexpectedly.
- DNS record monitoring: Checks A, AAAA and CNAME records and alerts you when they change without a planned update.
- Multi-location lookups: Shows whether DNS issues appear in one region, several regions or globally.
- Early alerts for failures: Notifies your team when lookups slow down, time out or return an unexpected IP address.
- Clear DNS behavior history: Provides charts and response data that show rising lookup times or intermittent failures before users notice.
Future of DNS security
DNS security is changing quickly as attackers adopt new techniques and organizations move more of their infrastructure to distributed cloud and edge environments. The risks are growing, but so are the tools available to defend against them. The next few years will bring several shifts that teams should prepare for.
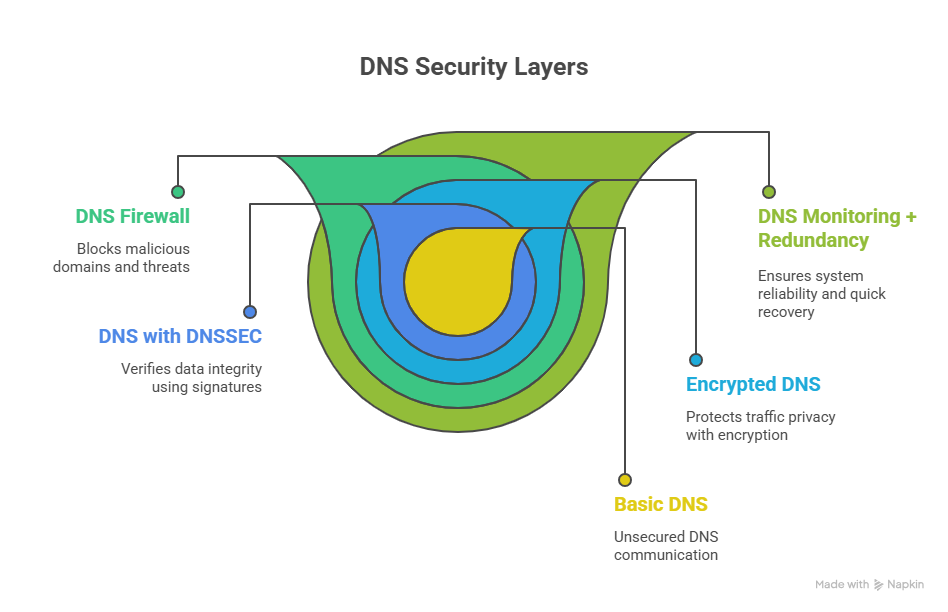
Encrypted DNS will become the default
Traditional DNS traffic is unencrypted, which makes it easy for attackers to intercept or modify responses. DNS over HTTPS and DNS over TLS are changing that model. As more browsers, ISPs and cloud networks adopt encrypted DNS, attempts at spoofing or man in the middle attacks become harder to execute.
Teams that operate their own DNS infrastructure should plan to support encrypted DNS at the resolver level. It improves both privacy and protection against common attack vectors.
DNSSEC adoption will continue to increase
DNSSEC adds cryptographic signatures to DNS records, which gives resolvers a way to confirm authenticity before accepting an answer. Adoption has historically been slow because of operational overhead, but more registrars and DNS providers now offer DNSSEC as a simple configuration option.
Signed zones are becoming a baseline expectation for businesses that depend on DNS for critical services. As more resolvers validate signatures by default, unsigned records will stand out as weaker links.
AI assisted detection will become more common
Attackers are relying more on domain generation algorithms, DNS tunneling and subtle reconnaissance techniques that hide within normal DNS traffic. Manual monitoring cannot keep up with these patterns.
Modern DNS security tools are beginning to use machine learning to identify anomalies such as:
- Sudden bursts of entropy heavy domain names
- Repeated low TTL lookups that are not tied to deployments
- Domains generated in large batches or predictable sequences
- High volume TXT or NULL queries
These systems help teams detect threats that would be difficult to recognize through logs alone.
DNS monitoring will integrate more deeply into observability workflows
DNS failures often appear as slow applications, broken APIs or inconsistent regional behavior. For many teams, DNS is still treated as an external dependency rather than a core part of the observability stack.
That is changing. Many modern tools now correlate DNS resolution times, record changes and regional inconsistencies with application and network data. This makes it easier to identify the real cause of an outage and respond faster.
What to expect going forward
DNS attacks are becoming more sophisticated, and infrastructure is becoming more distributed. The organizations that adapt fastest will be the ones that treat DNS as a first class part of their security and monitoring strategy.
Encrypted DNS, signed zones, behavioral analytics and continuous monitoring create a stronger baseline that helps teams detect threats early and maintain reliable services.
Conclusion
DNS sits at the front of every request your users make. When attackers target it, the impact spreads quickly: slow lookups, broken pages, misrouted traffic or complete outages. The best defense is a mix of strong configuration, secure registrar access, redundancy and continuous monitoring.
When you know how DNS attacks work and what early warning signs look like, you can respond before the problem reaches your customers. UptimeRobot can help your team stay ahead by watching DNS records, tracking resolution patterns and alerting your team the moment something changes.
Strengthen your DNS setup, monitor it from multiple locations and make DNS part of your broader security and observability workflow. These steps give you earlier visibility, faster responses and fewer surprises during incidents.
FAQ's
-
DNS attacks usually come from attempts to redirect traffic, take services offline or extract data. Attackers target weak DNS configurations, unsecured registrar accounts, outdated name servers, open resolvers or networks that accept forged DNS responses. Some attacks also begin with broader network events such as BGP route hijacks that divert DNS traffic to malicious servers.
-
No, but you can make them far harder to execute. Strong configuration, DNSSEC, protected registrar access, redundant name servers and continuous monitoring significantly reduce the risk. These controls help you block common vectors and spot suspicious behavior before it impacts users.
-
DNS poisoning happens when a resolver caches a forged DNS record and returns the wrong IP address to users. DNS hijacking changes the DNS path itself, often by modifying registrar settings, intercepting DNS traffic or redirecting queries to servers controlled by the attacker. Poisoning targets caches, while hijacking targets the infrastructure behind them.
-
Look for unusual DNS error patterns such as NXDOMAIN or SERVFAIL spikes, slower than normal resolution times, unexpected changes to DNS records or inconsistent IP results across regions. You may also see higher application latency, failed lookups or traffic drops from specific locations. DNS monitoring helps reveal these issues early.
-
The best tool depends on your stack, but the key features to look for are multi location checks, record change alerts, fast resolution testing and clear visibility into DNS behavior. UptimeRobot monitors DNS records, checks resolution consistency and alerts you when something changes unexpectedly, which helps you react before users notice a problem.